Security for AI
We asked 500 security professionals their opinions about AI
We asked 500 security professionals their opinions about AI
of security professionals said that GenAI was one of the most significant risks they saw impacting their organization
of respondents believe GenAI will have a major impact on their organization
are confident in their ability to secure its use
believe that AI legislation will help enhance safety and security
are concerned about the reputational risks tied to AI
highlight that basic security practices are being overlooked in the rush to implement GenAI
Forward-thinking organizations are taking proactive steps to avoid AI-related security incidents. AI red teaming—where organizations invite security researchers to identify safety and security flaws in their AI products—is gaining traction as a best practice for testing GenAI deployments.
What’s the difference between AI safety and AI security?
AI safety focuses on preventing AI systems from generating harmful content, from instructions for creating weapons to offensive language and inappropriate imagery. It aims to ensure responsible use of AI and adherence to ethical standards.
AI security involves testing AI systems with the goal of preventing bad actors from abusing the AI to, for example, compromise the confidentiality, integrity, or availability of the systems the AI is embedded in.
AI Safety Programs
$401average payout
AI Security Programs
$689average payout
Establish continuous testing, evaluation, verification, and validation throughout the AI model life cycle.
Establish an AI governance framework outlining roles, responsibilities, and ethical considerations, including incident response planning and risk management.
Train all users on ethics, responsibility, legal issues, AI security risks, and best practices such as warranty, license, and copyright.
Get researcher insights, customer testimonials, industry data, analysis and advice, and more.

AI and automation are powerful efficiency tools.
average saved by organizations per breach1
We surveyed 2000 members of our security researcher community about their use of AI
of security researchers see AI as an essential part of their work
of security researchers reported using AI in some capacity
33% of security researchers are using AI to summarize information and write reports. You can also use AI to streamline and enhance your vulnerability management process via HackerOne’s GenAI copilot, Hai.
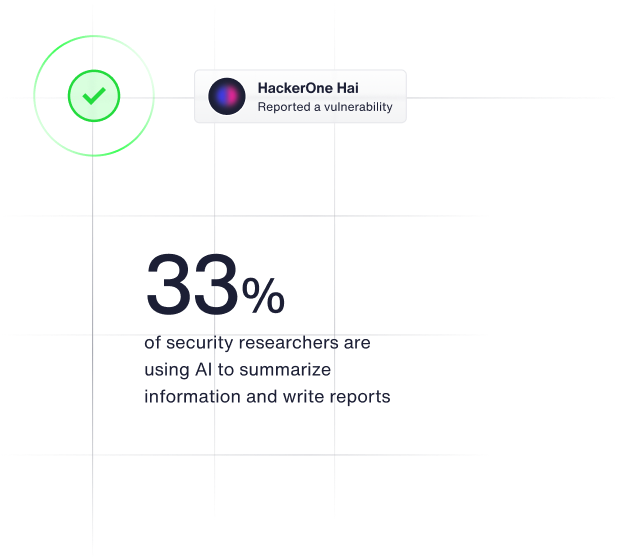
Use Hai’s tailored advice to quickly interpret complex vulnerability reports with concise summaries and deeper insights for faster decision-making.
Use Hai to also craft clear and succinct messages for effective communication between security, development teams, and researchers.
Automate tasks by integrating Hai for to assist with writing assistance, generating custom vulnerability scanner templates, and managing large reports, reducing manual effort.