04
Beyond Bounties: What Makes a High-Performance Program
of researchers say bounties attract them to a program
of researchers say they are turned off by low bounties
What attracts researchers to a program?
What turns them off about a program?
Beyond the financial aspect, researchers value:
Strong relationships with security teams
Transparent communication
Quick bounty payments and report resolutions
Recommendations
Focus researchers’ efforts on the most critical components of your attack surface. These could be assets that have stagnant testing, lack attention, are new feature investments, or are recent acquisitions.
Offer more advanced testing opportunities with unique scope or access to gated assets.
Provide researchers with additional documentation to clarify scope, free test accounts, or even company swag to maximize impact without solely relying on increased bounties.
Download the Full 8th Annual Hacker-Powered Security Report
Get researcher insights, customer testimonials, industry data, analysis and advice, and more.

Top-performing programs have three key traits:
(Top-performing programs are those with more than 30% of valid vulnerability submissions rated high or critical.)
Higher bounties
Offering average payouts of $3,300 at the 95th percentile, compared to $2,000 for lower-impact programs.
Smaller, focused communities
Engaging fewer researchers, with an average of 56 versus 97 in lower-impact programs. However, being able to curate a smaller, highly engaged group depends on having a large researcher pool from which to choose the most applicable talent for your program.
Broader testing scope
Providing more assets for testing, averaging 60 assets compared to 34 in lower-impact programs.
Recommendations
Collaborate with a select group of skilled researchers who align well to your program’s scope.
Establish reward structures aligned with the criticality of the assets being tested, ideally offering compensation above market standards.
Ensure your testing scope is broad and varied, allowing researchers with diverse skill sets to contribute meaningfully. This targeted approach fosters deeper engagement and drives more impactful security outcomes.
Budgeting for Bounties
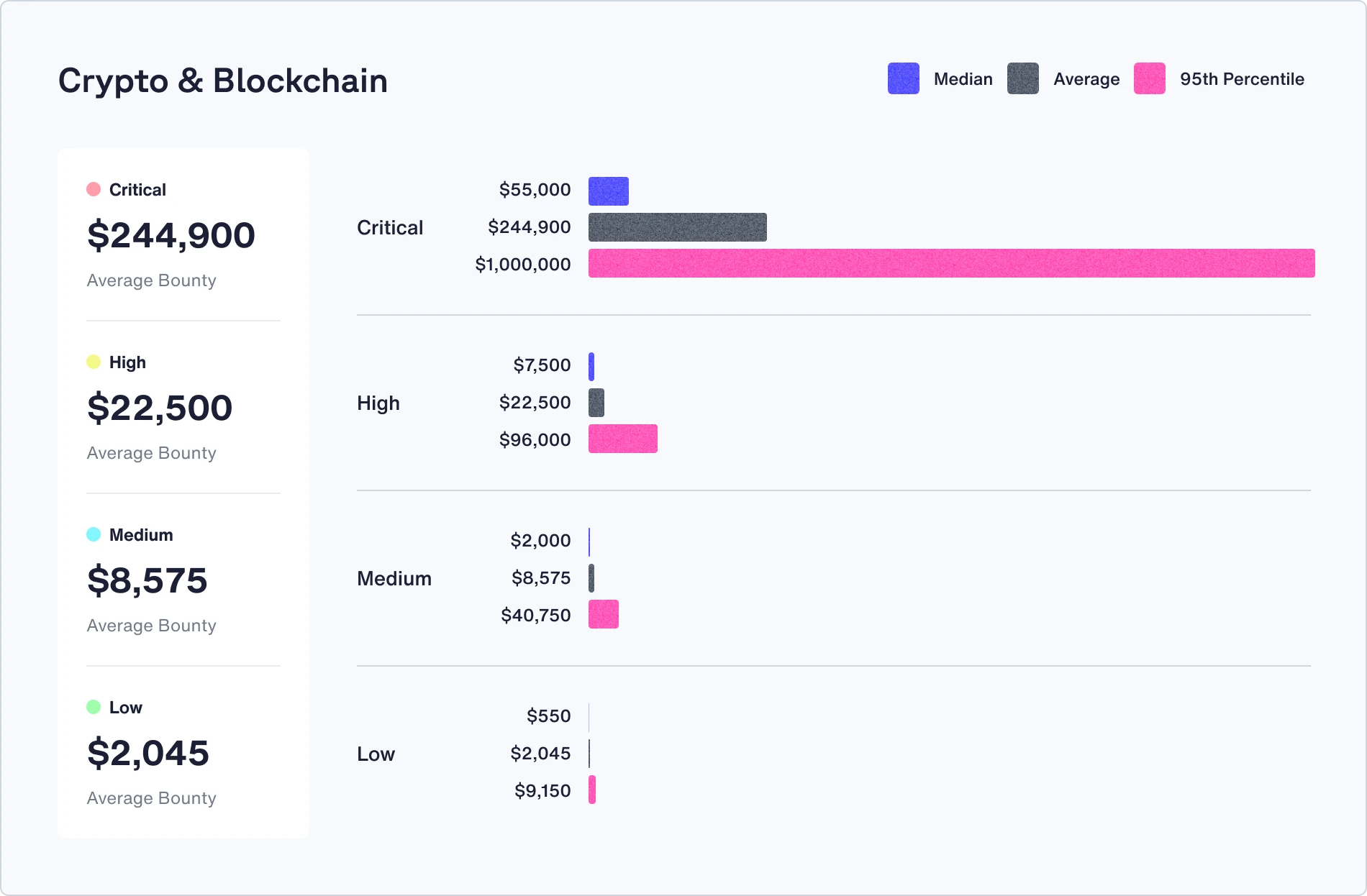
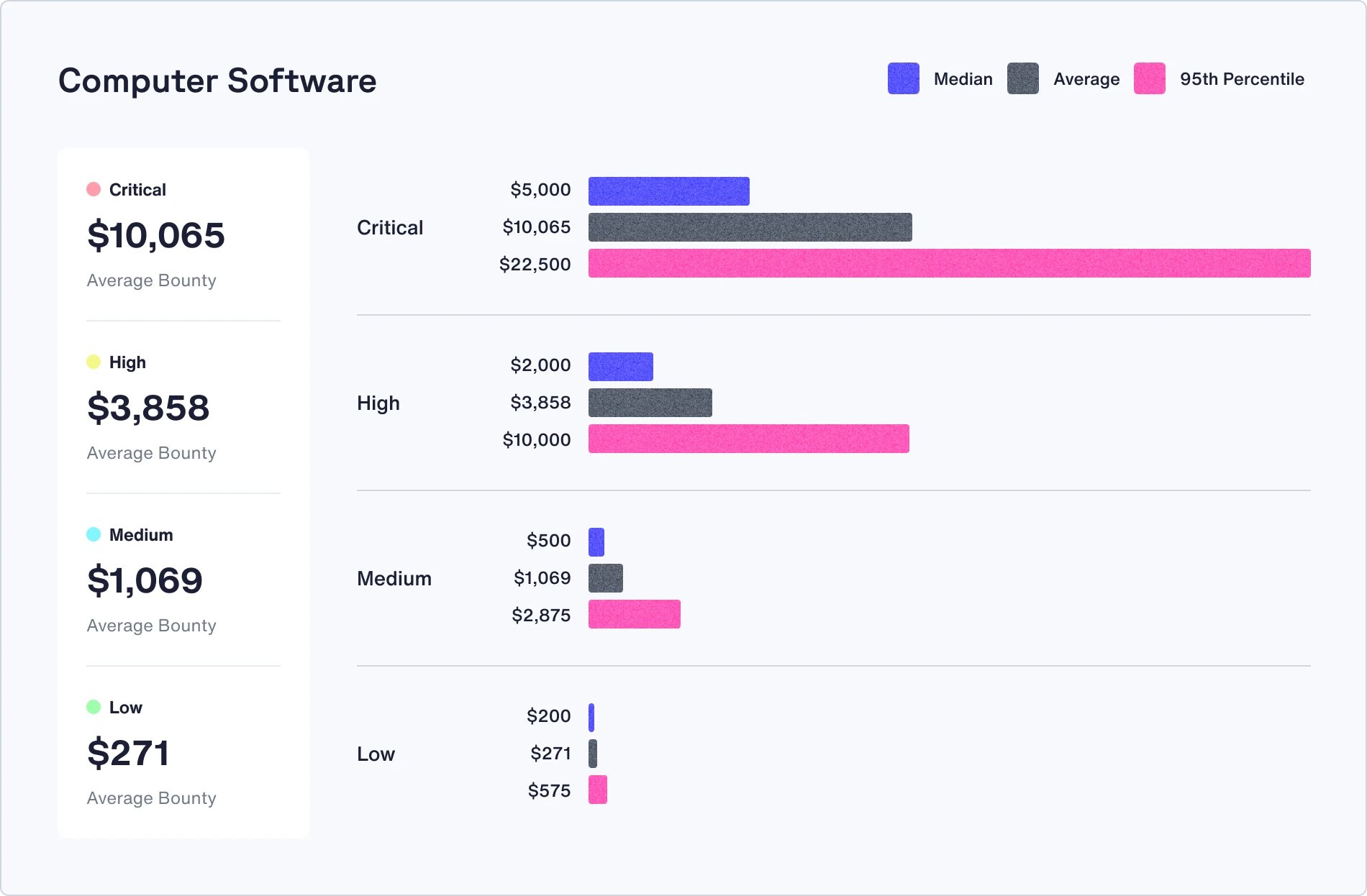
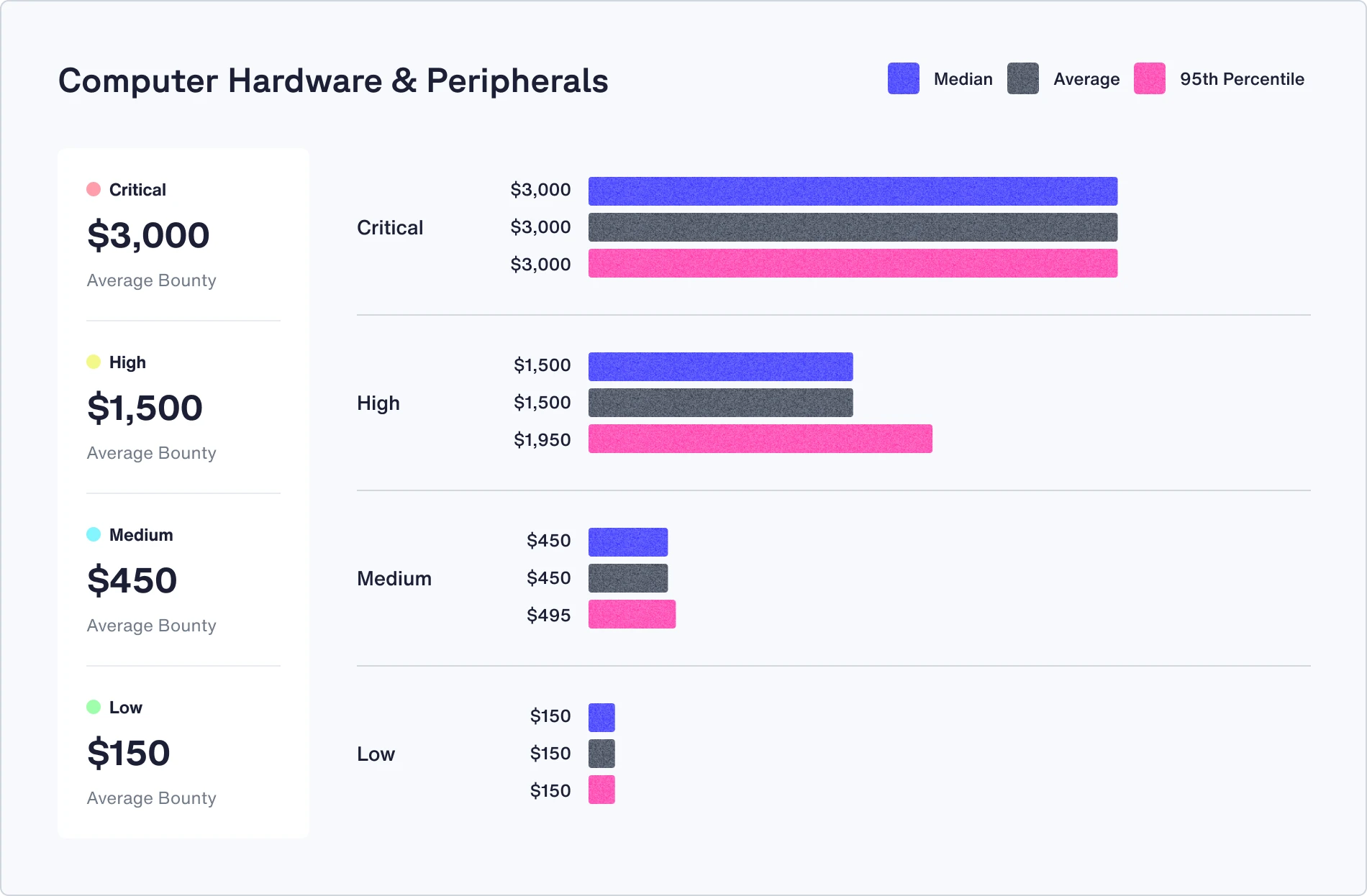
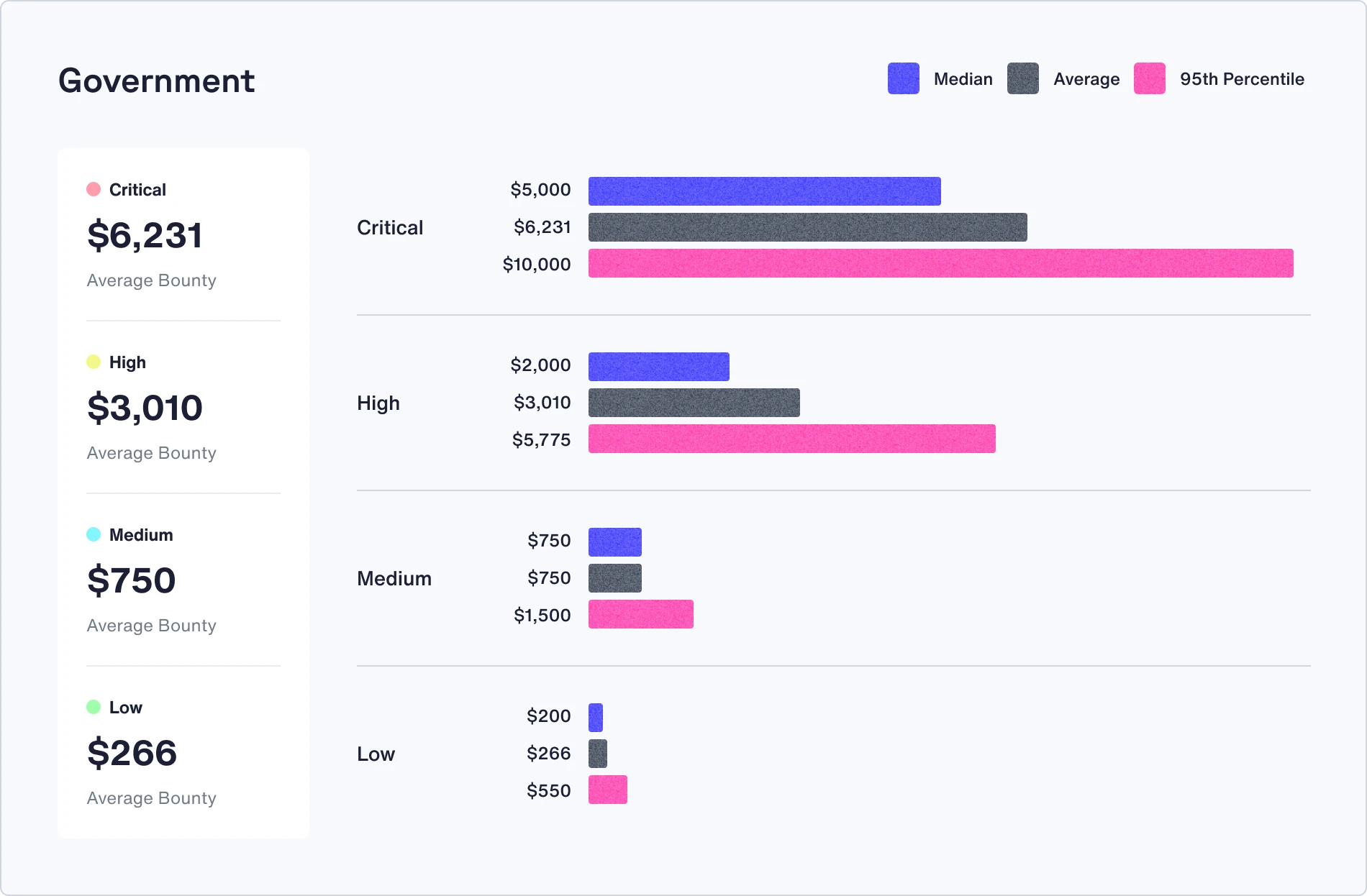
Bounties can make or break a bug bounty program. Average bounty payouts have remained steady over the past 12 months, with a 5% increase year over year, from $1,066 to $1,116.
Without competitive compensation, talented researchers may move to more lucrative programs, or focus only on low-hanging fruit that doesn’t require detailed research effort, resulting in less exploitable, less critical vulnerabilities.
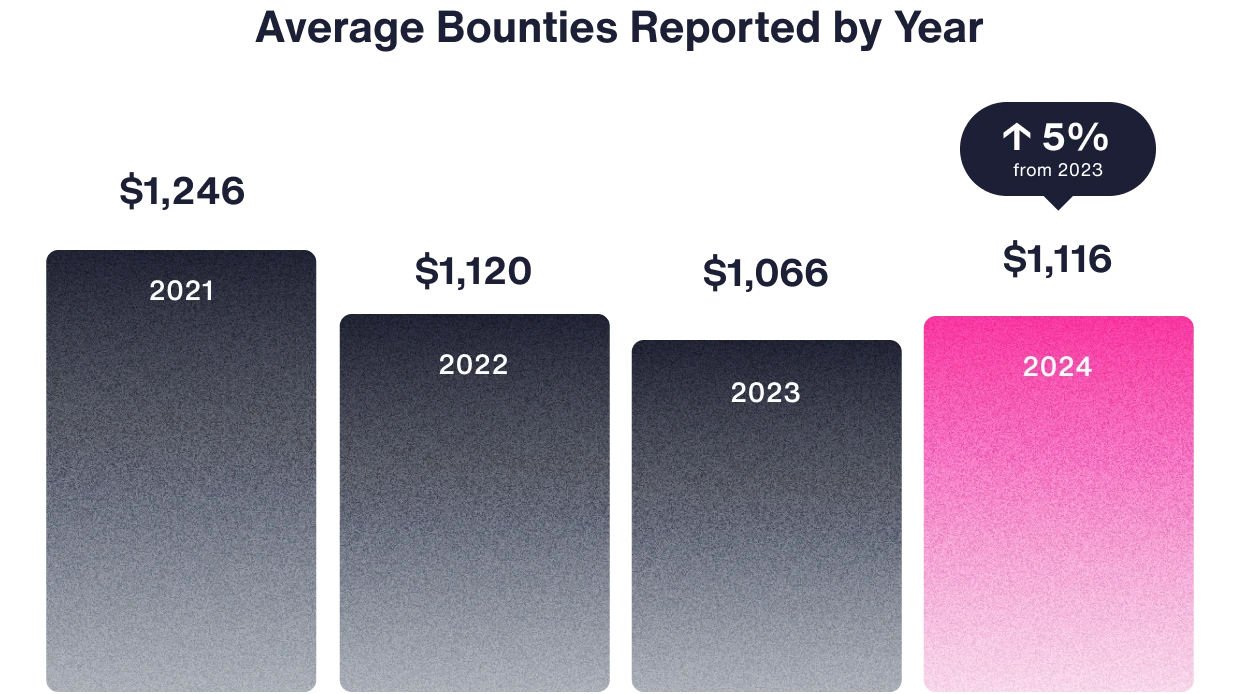
Check out the median, average, and 95th percentile bounties in your industry
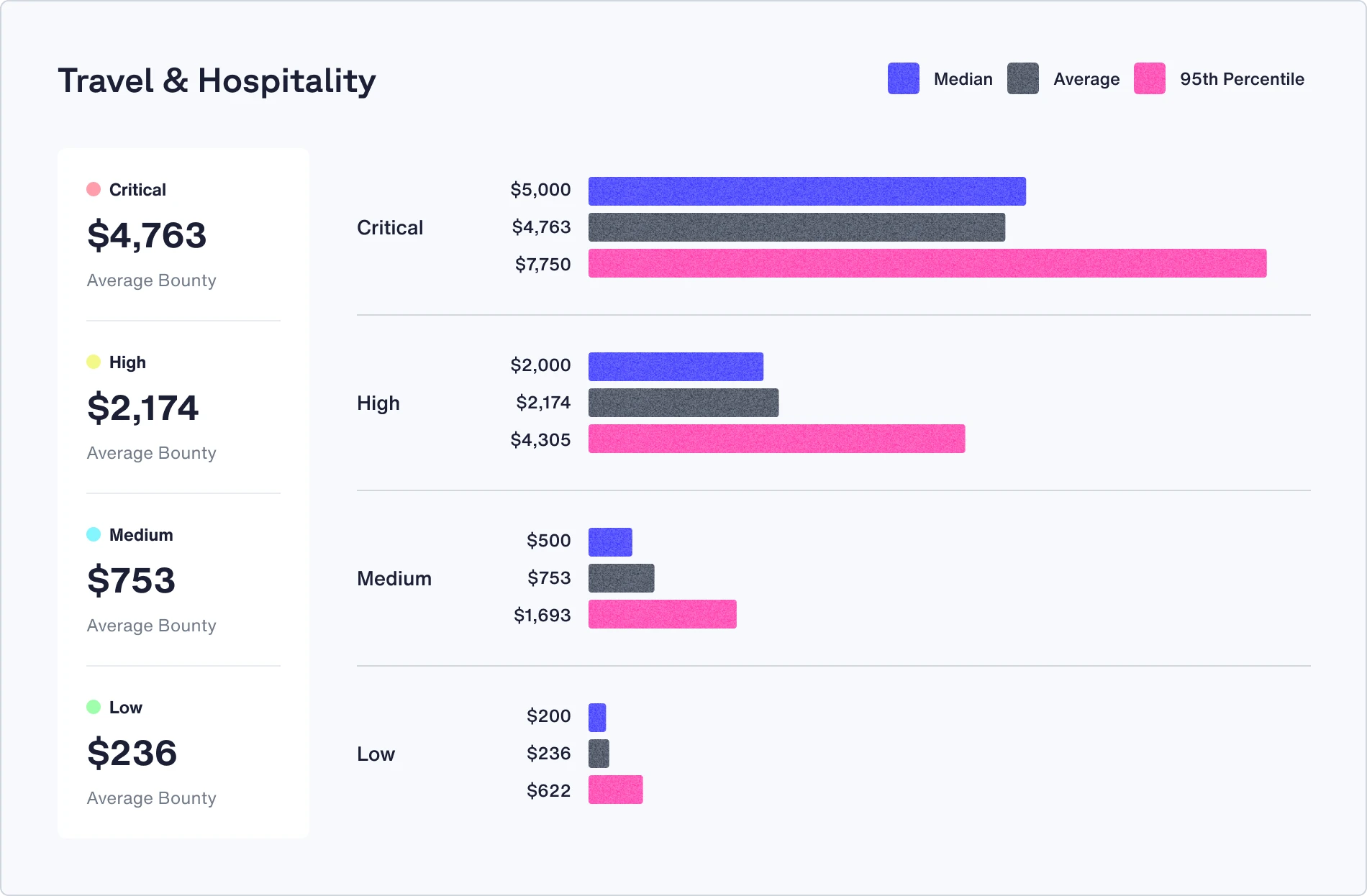
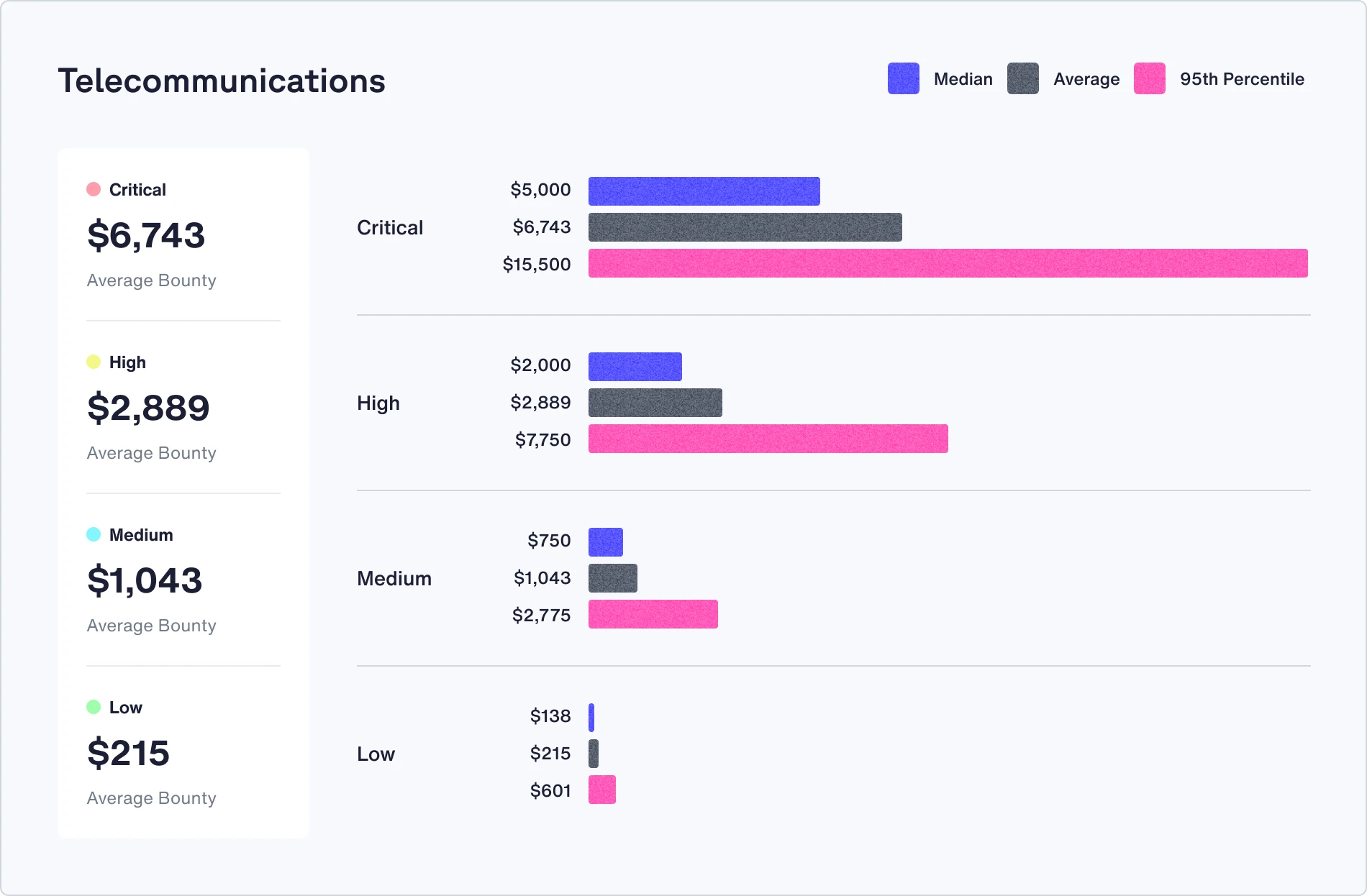
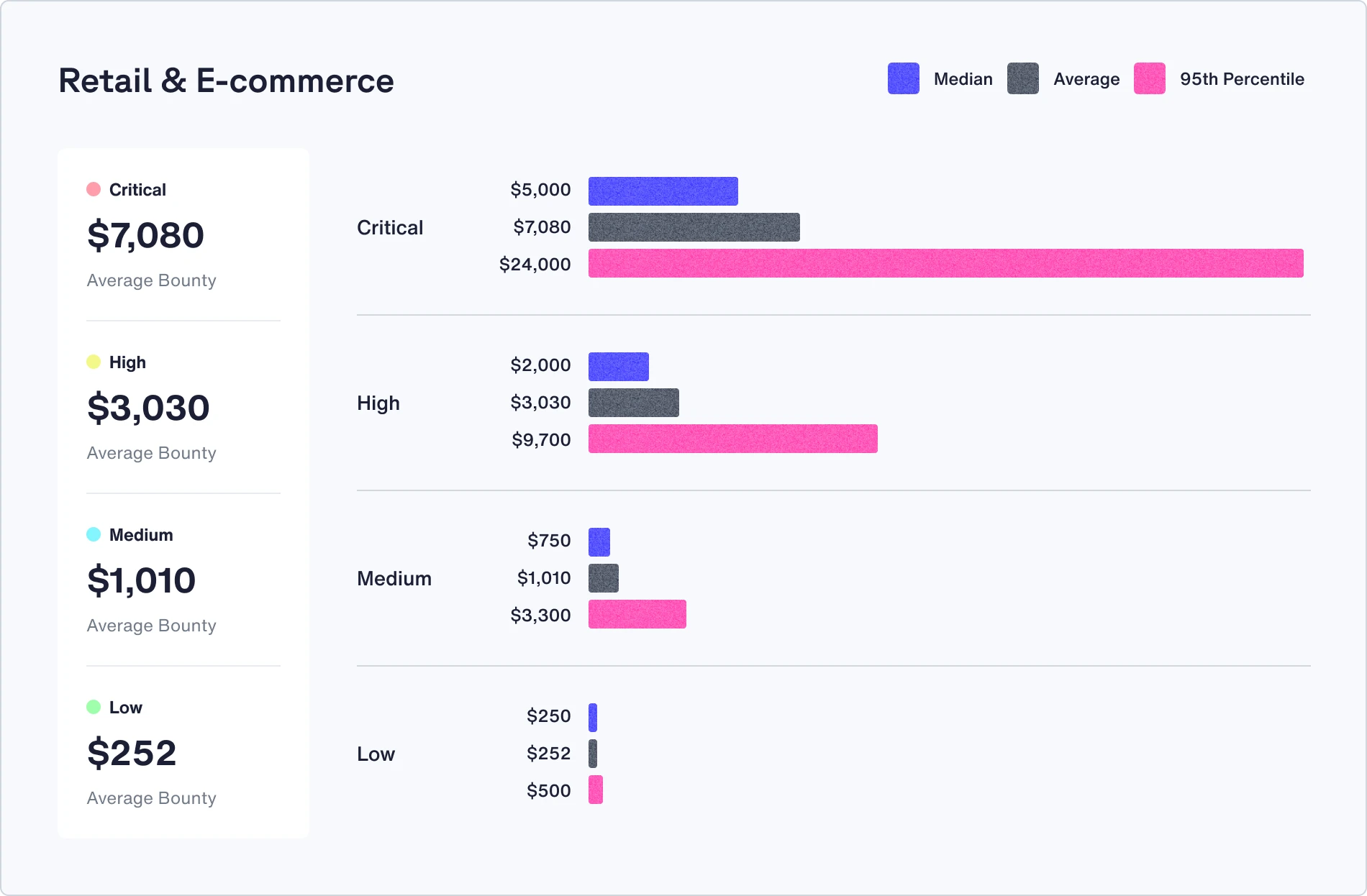
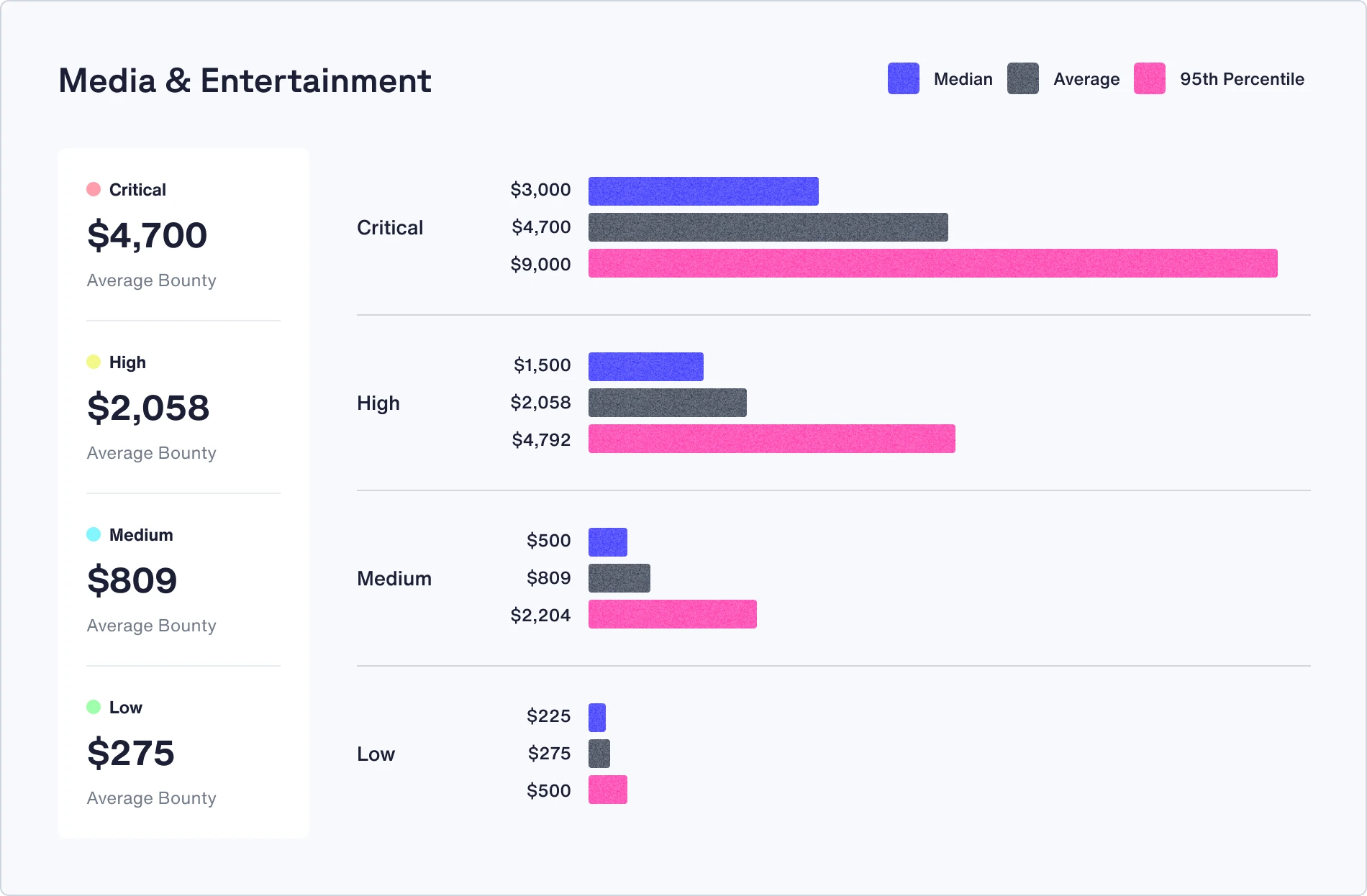
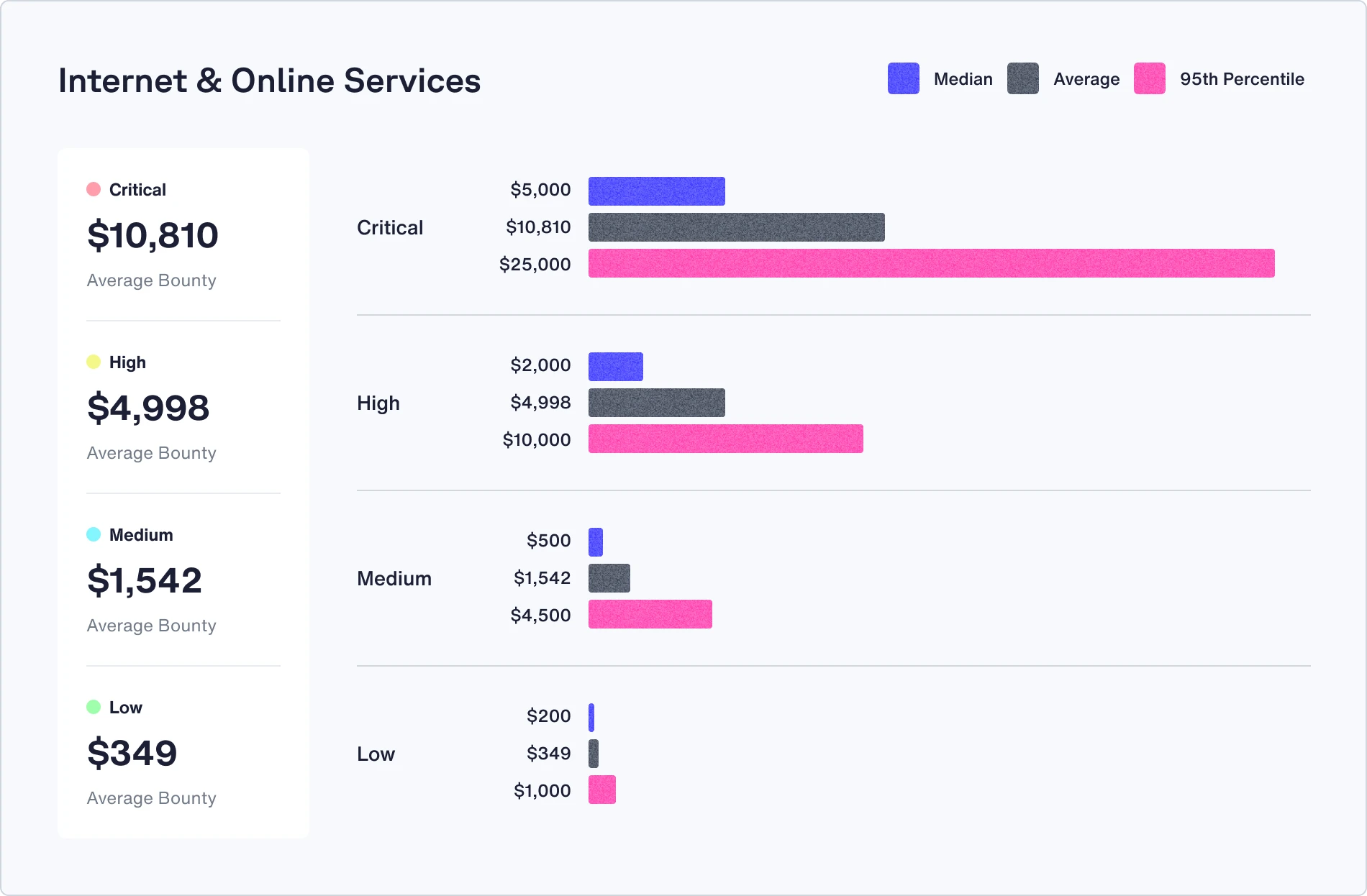
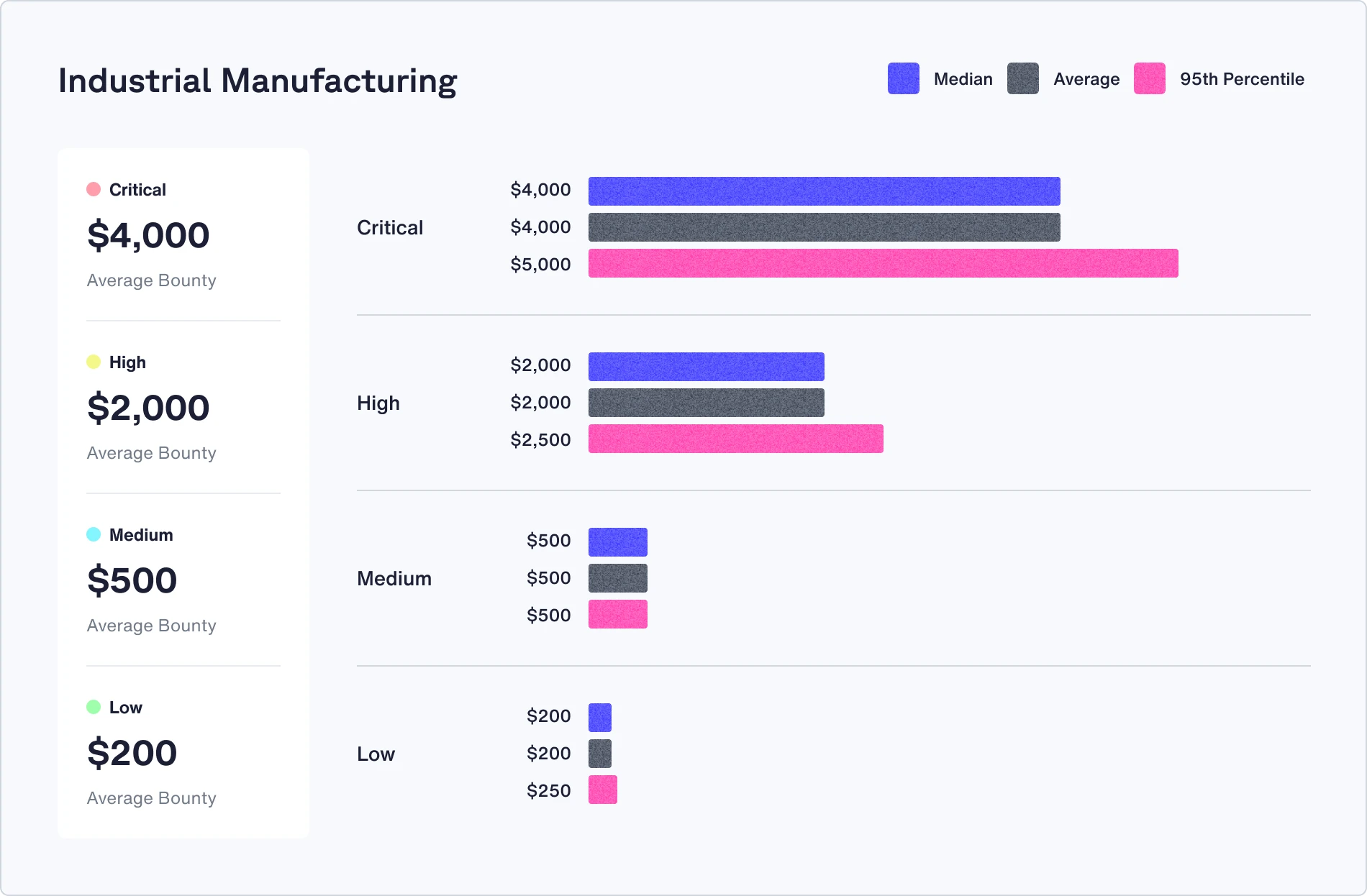
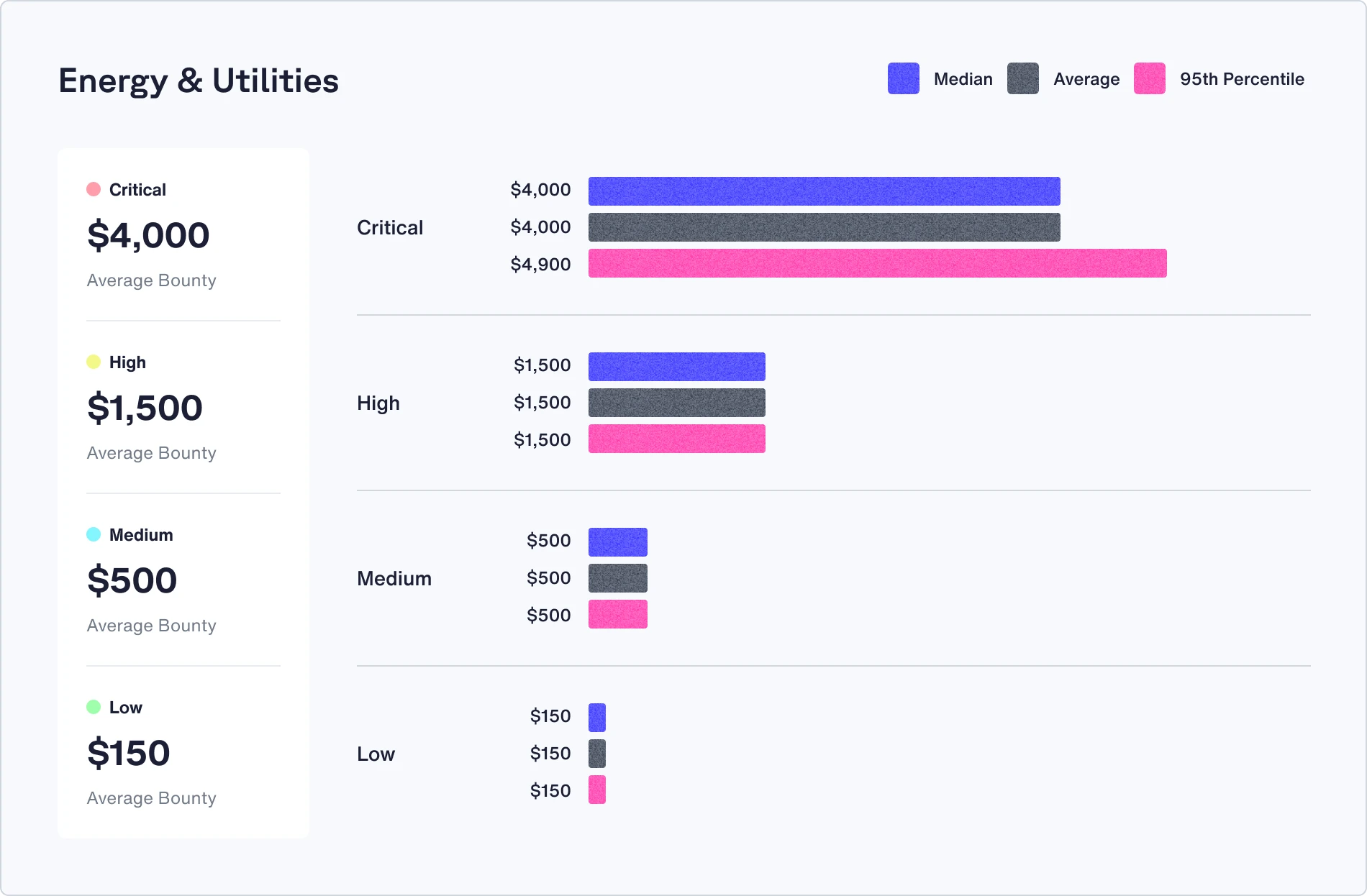
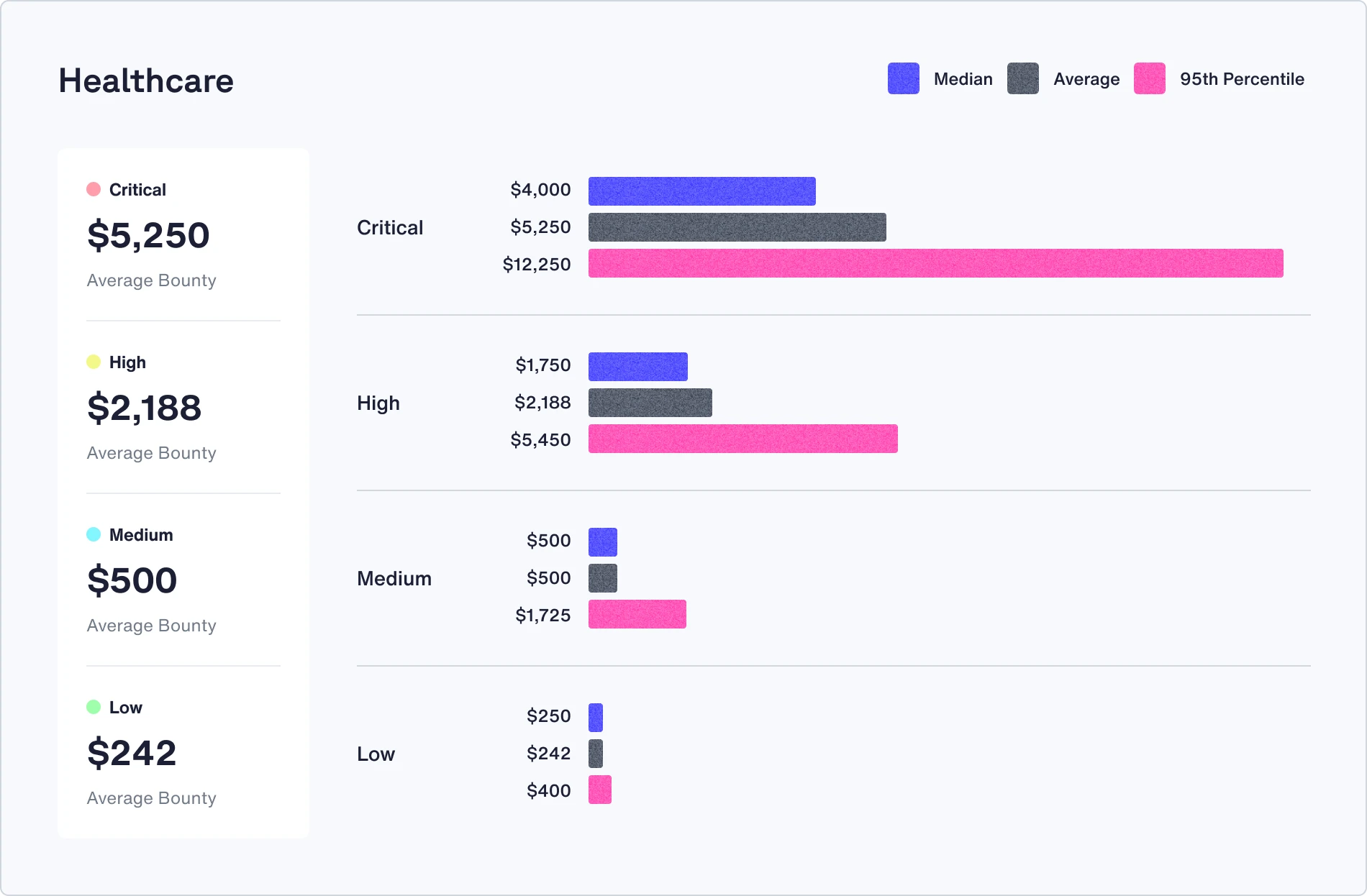
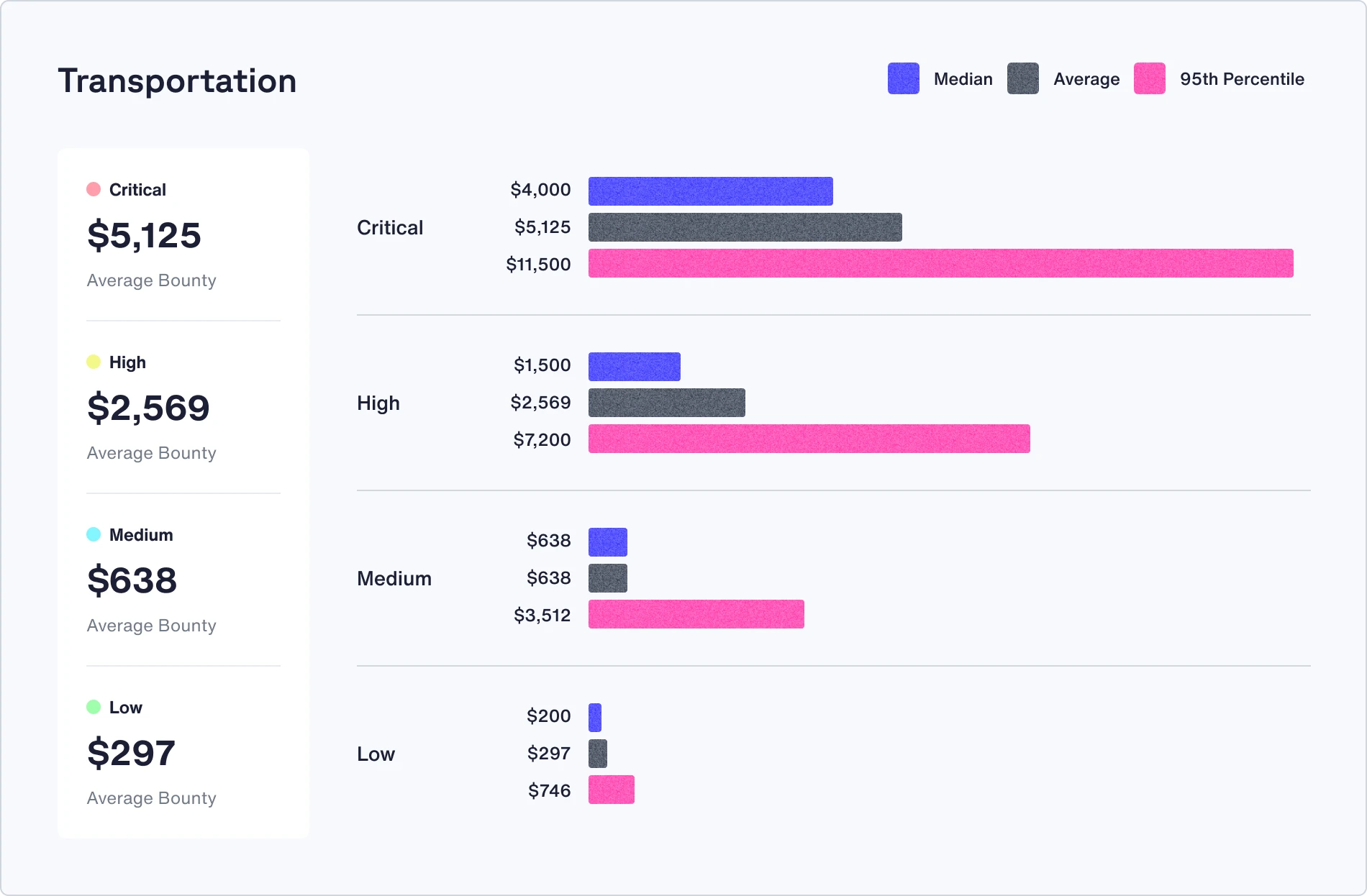
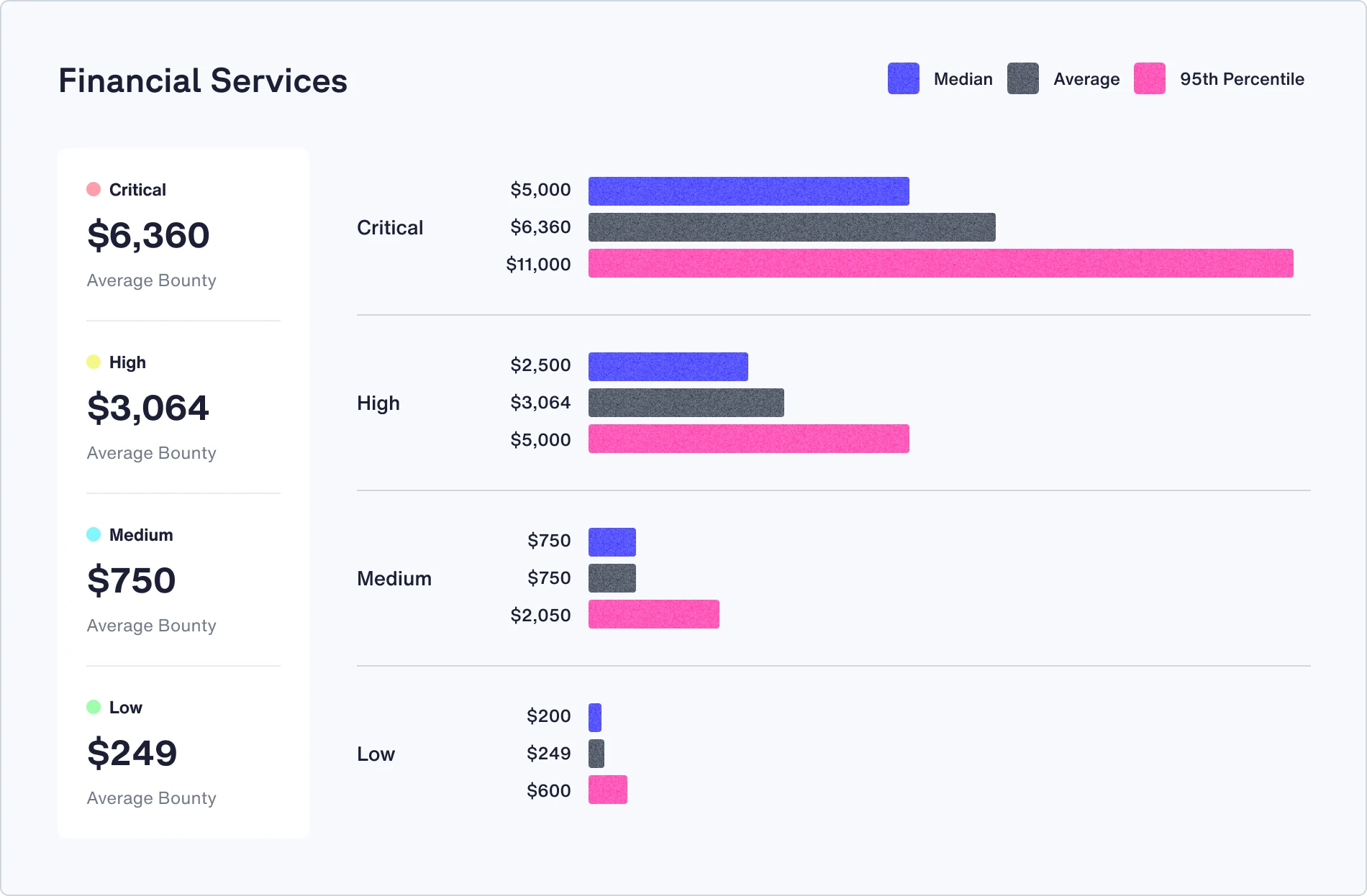
Recommendations
Make a strong business case for your budget that speaks to the priorities of your stakeholders and board members. Check out the Measuring Success section of this report to see how the most security-resilient organizations are making the financial case for their bounty budgets using a "return on mitigation" (ROM) approach.
Take a tiered-award approach with bounty awards weighted by asset type. Bounty award amounts can be adjusted to incentivize testing on your most critical assets and assets that may require a more unique skill set.
Set bounties high enough to attract interest. If you're falling behind your budget and not receiving reports on business-critical assets, it's a clear sign that your bounties may need adjustment.
