05
Explore Your Top Ten Vulnerabilities
valid issues were found across 1,300+ customer programs
of these are rated high or critical
Number of Valid Reports by Year
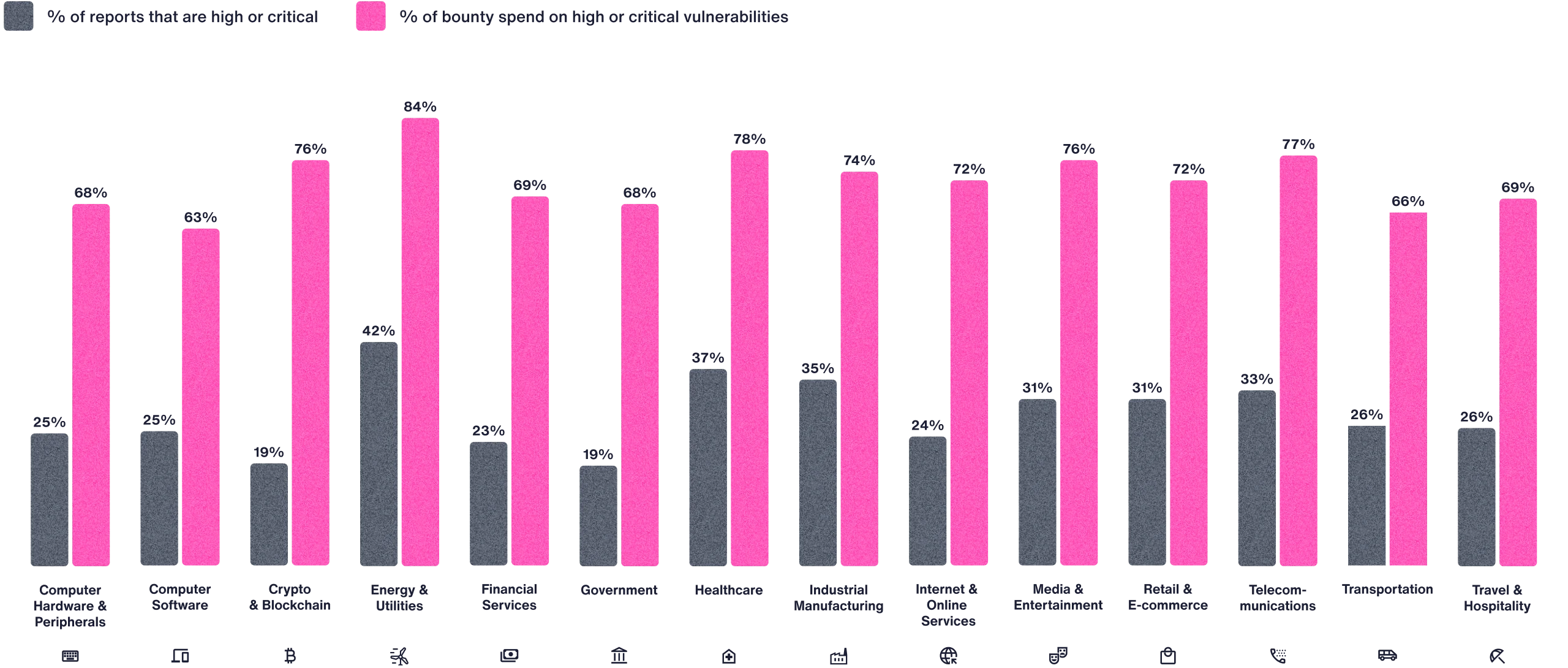
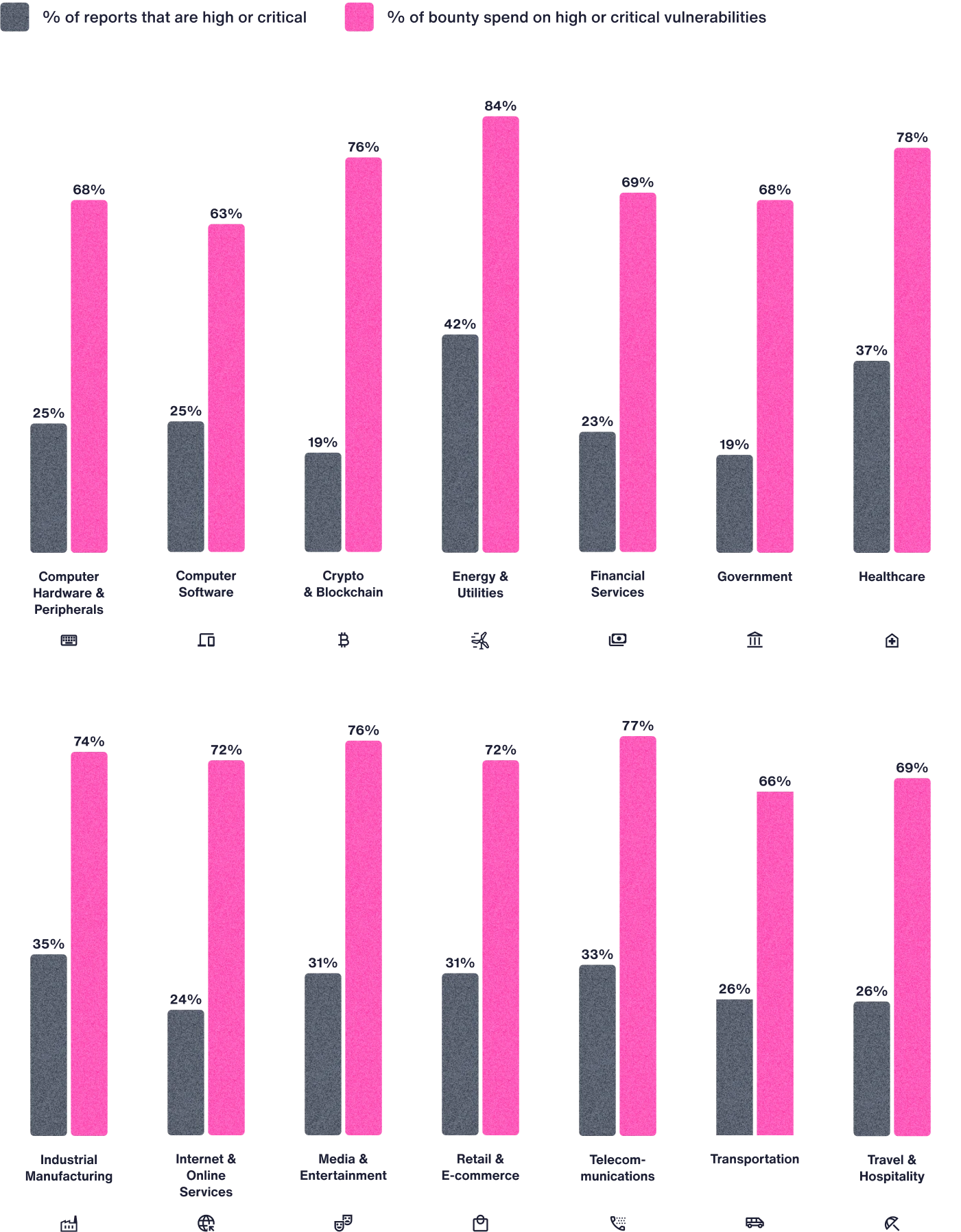
What Percentage of Vulnerability Reports Are High or Critical For Your Industry?
Vulnerabilities are too often seen as just part of the tech landscape.
“We don’t have a cybersecurity problem. We have a software quality problem.”
– Jen Easterly, Director of CISA
The industry needs a shift toward building software with security as a priority.
The good news? There’s a clear path to stronger security. HackerOne data shows that the top ten vulnerabilities reported to customer programs are common and mostly preventable with proactive measures. Catching these issues early in the SDLC can significantly cut down on bounty costs. Check how your industry stacks up against the average for common vulnerabilities and how you can mitigate against them.
Download the Full 8th Annual Hacker-Powered Security Report
Get researcher insights, customer testimonials, industry data, analysis and advice, and more.

The Top Ten Vulnerabilities Reported to Customer Programs
Deep Dive on Your Industry
Financial Services
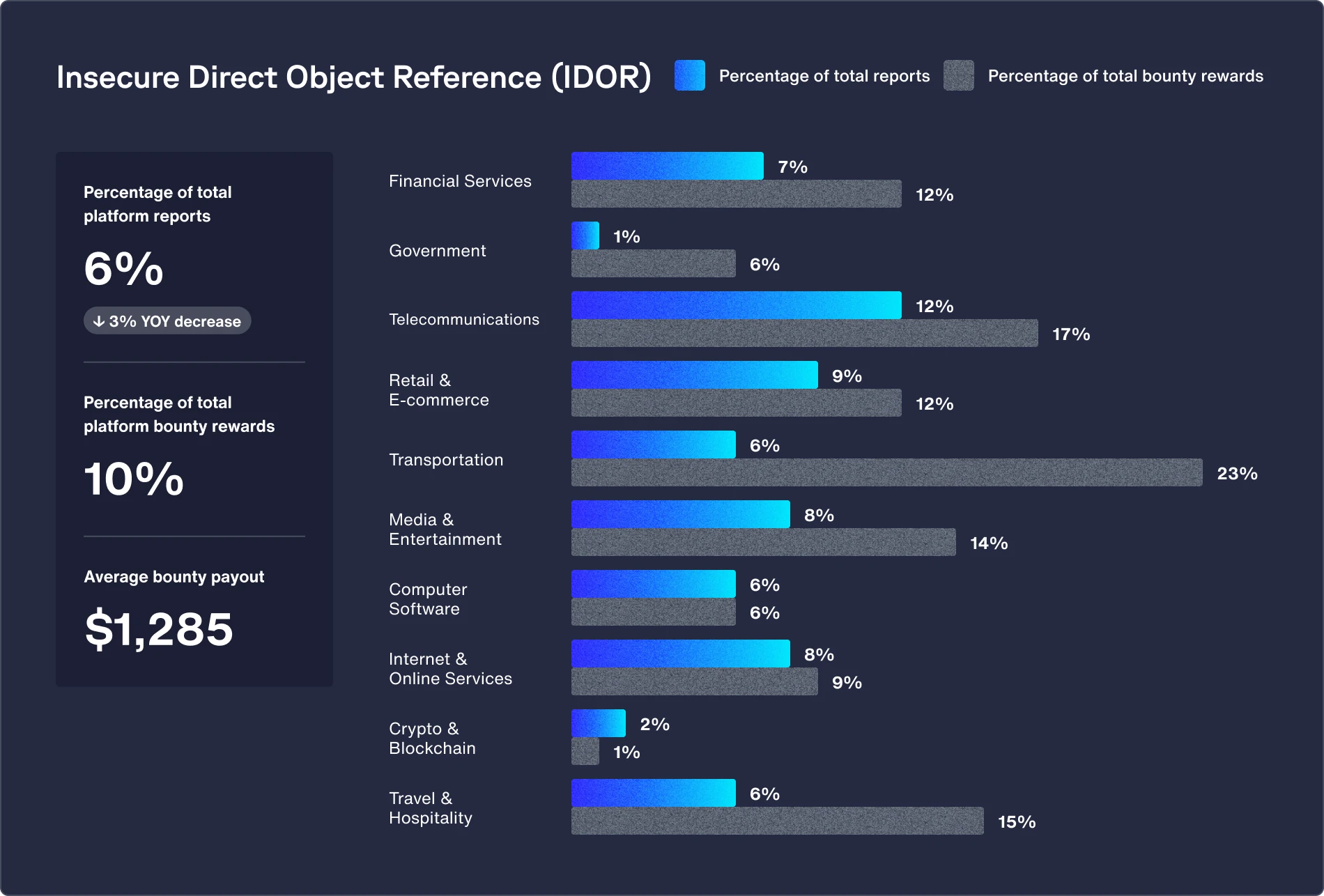
Featured vulnerability: Insecure direct object reference (IDOR) (up 47% from 2023)
IDOR (insecure direct object reference) vulnerabilities are particularly prevalent in financial services because of their complex, multi-layered applications that manage sensitive data, like personal financial information and transactions. The frequent user actions, such as money transfers and account access, heighten the risk of IDOR exploits when access controls are weak, making them prime targets for bug bounty hunters.
Recommendations:
- Implement a strong authorization framework that relies on user policies and hierarchy and validate authorization for every request that involves accessing sensitive objects or resources.
- Avoid using functions that automatically bind a client’s input into variables, internal objects, or object properties.
- Use indirect, random, and unique identifiers instead of exposing direct references to internal objects and resources. Map these identifiers to the actual objects on the server side while validating and authorizing user-supplied input.
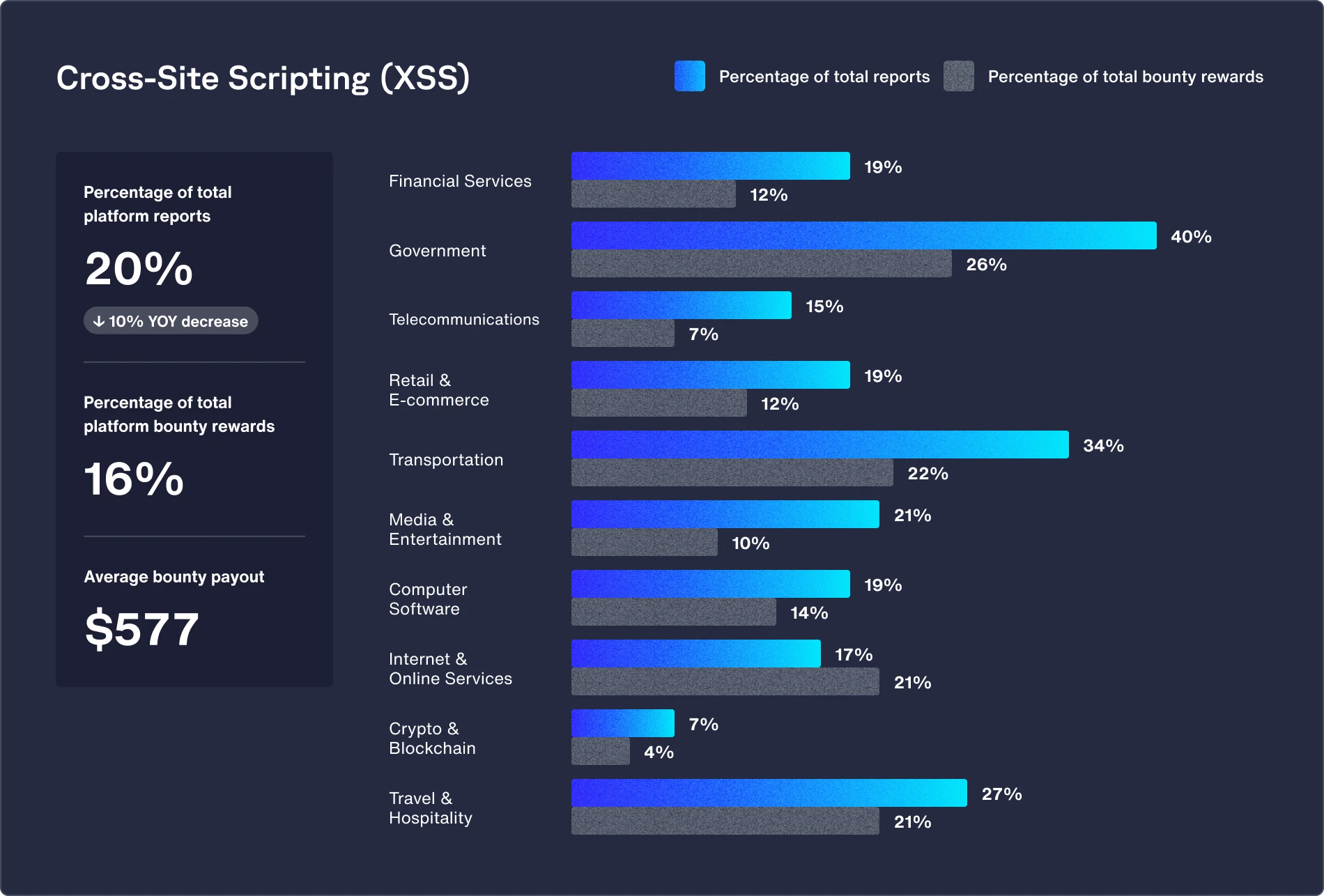
Government
Featured vulnerability: Cross-site scripting (XSS) (up 17% from 2023)
Government agencies see a much higher rate of XSS vulnerability reports than the industry average. This is likely due to their many complex web environments, as they manage a wide range of websites and services for various public functions.
Recommendations:
- Treat all input as malicious and create a list of what is expected or valid input.
- Encode output that, depending on the output context, might require applying combinations of HTML, URL, JavaScript, and CSS encoding.
- Implement a content security policy (CSP) to restrict the sources of executable scripts and limit the potential impact of XSS attacks.
Telecommunications
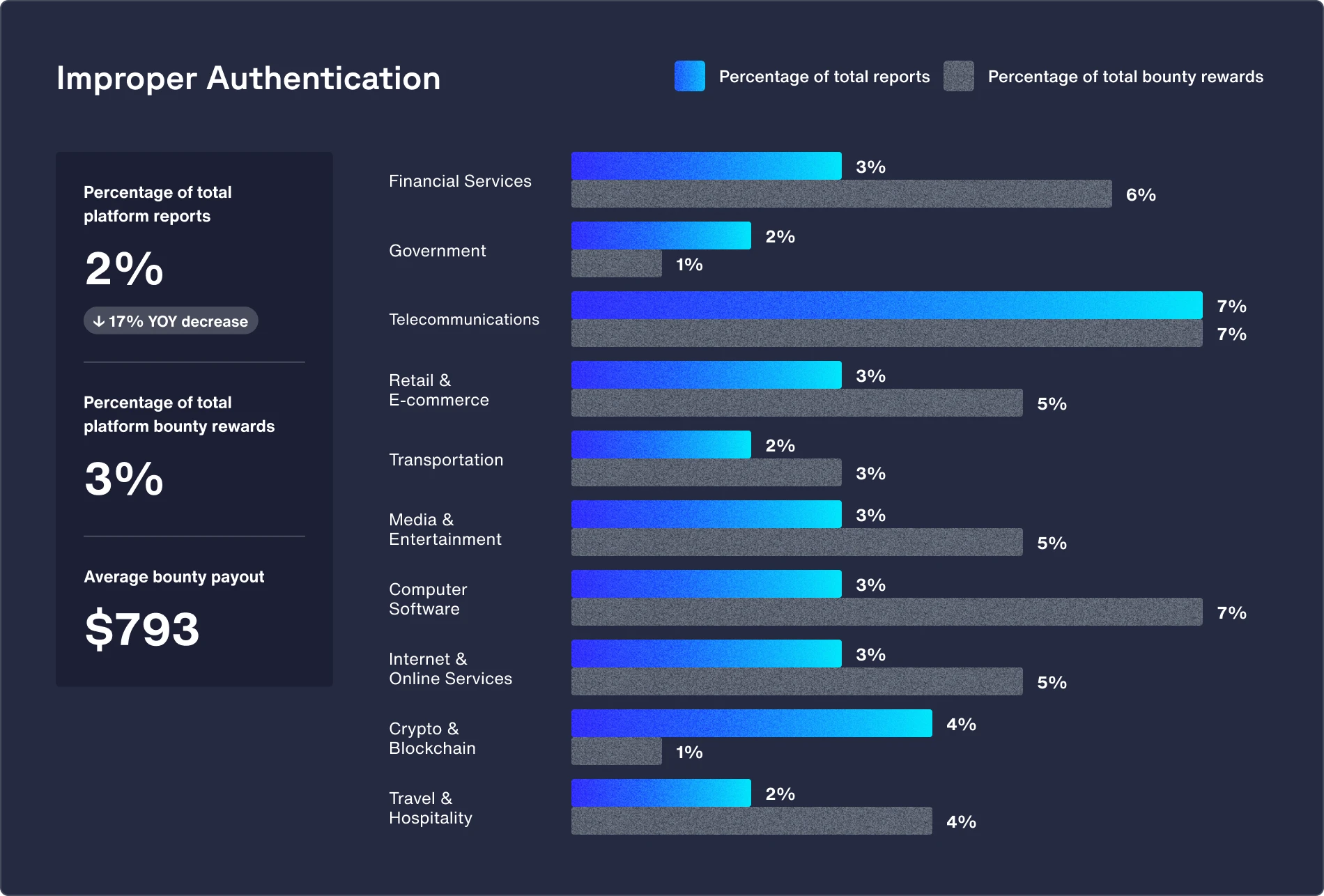
Featured vulnerability: Improper authentication (up 55% from 2023)
Telecom organizations manage vast networks with millions of connected users and devices, making authentication across such a complex infrastructure prone to misconfigurations or weak implementations.
Recommendations:
- Implement robust and secure authentication methods, such as strong password requirements, multi-factor authentication (MFA), secure password storage, and account lockout mechanisms.
- Manage session and authentication tokens by generating random, unique, and unpredictable tokens, securely storing them on the server side, implementing proper session expiration and logout mechanisms, and avoiding persistent tokens unless necessary.
- Avoid exposing unnecessary data in APIs, error messages, or logs, and use generic error messages to prevent attackers from gaining insights.
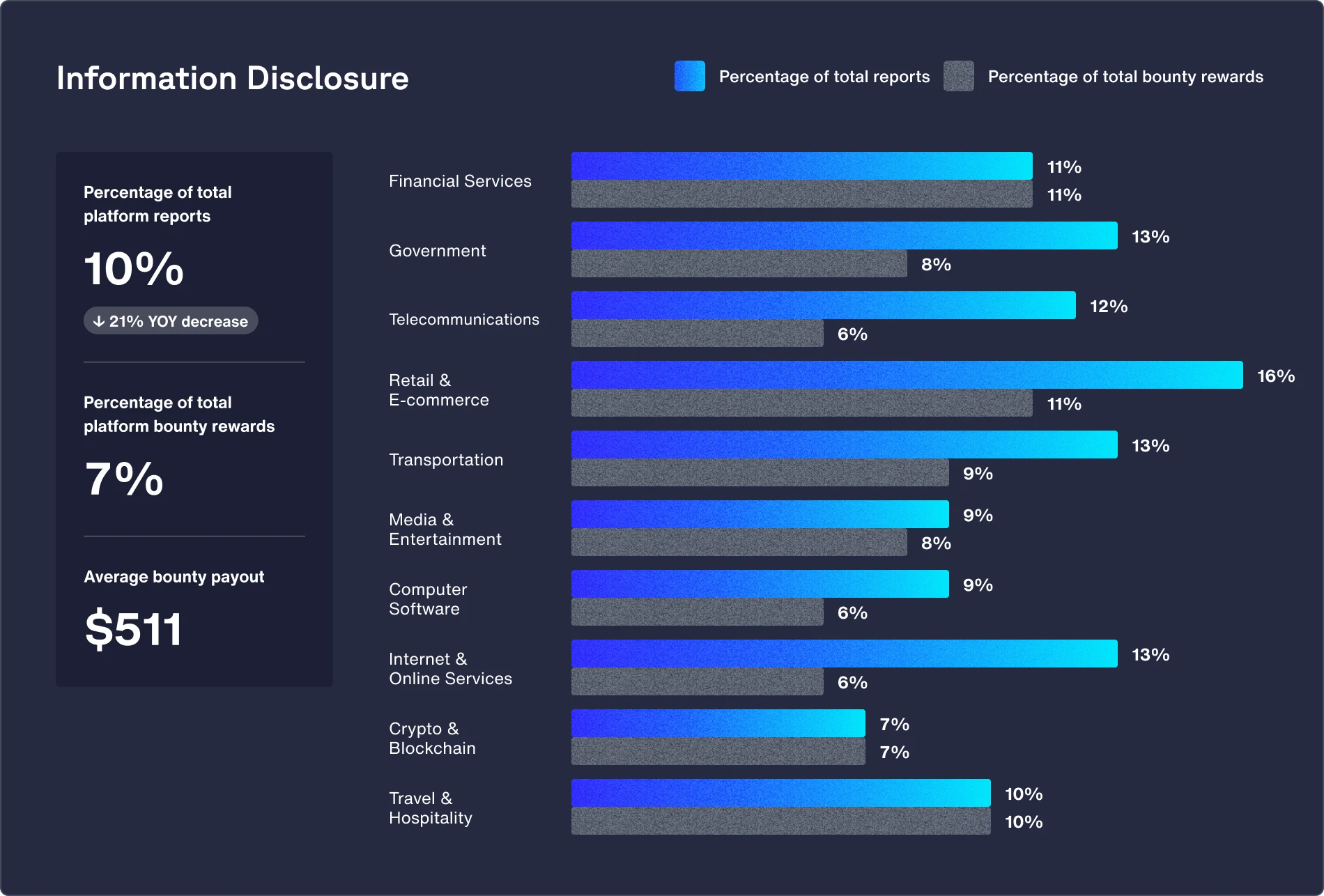
Retail & E-commerce
Featured vulnerability: Information disclosure (up 71% from 2023)
The complexity of e-commerce platforms, featuring dynamic websites and applications, increases the risk of information leaks through improperly secured APIs, mishandled user inputs, and flawed data management practices.
Recommendations:
- Ensure that sensitive data, such as user credentials, payment details, and personal information, is encrypted in transit and at rest.
- Avoid exposing unnecessary data in APIs, error messages, or logs, and use generic error messages to prevent attackers from gaining insights.
- Follow the principle of least privilege. Grant users and processes the minimum permissions necessary to perform their tasks.
Transportation
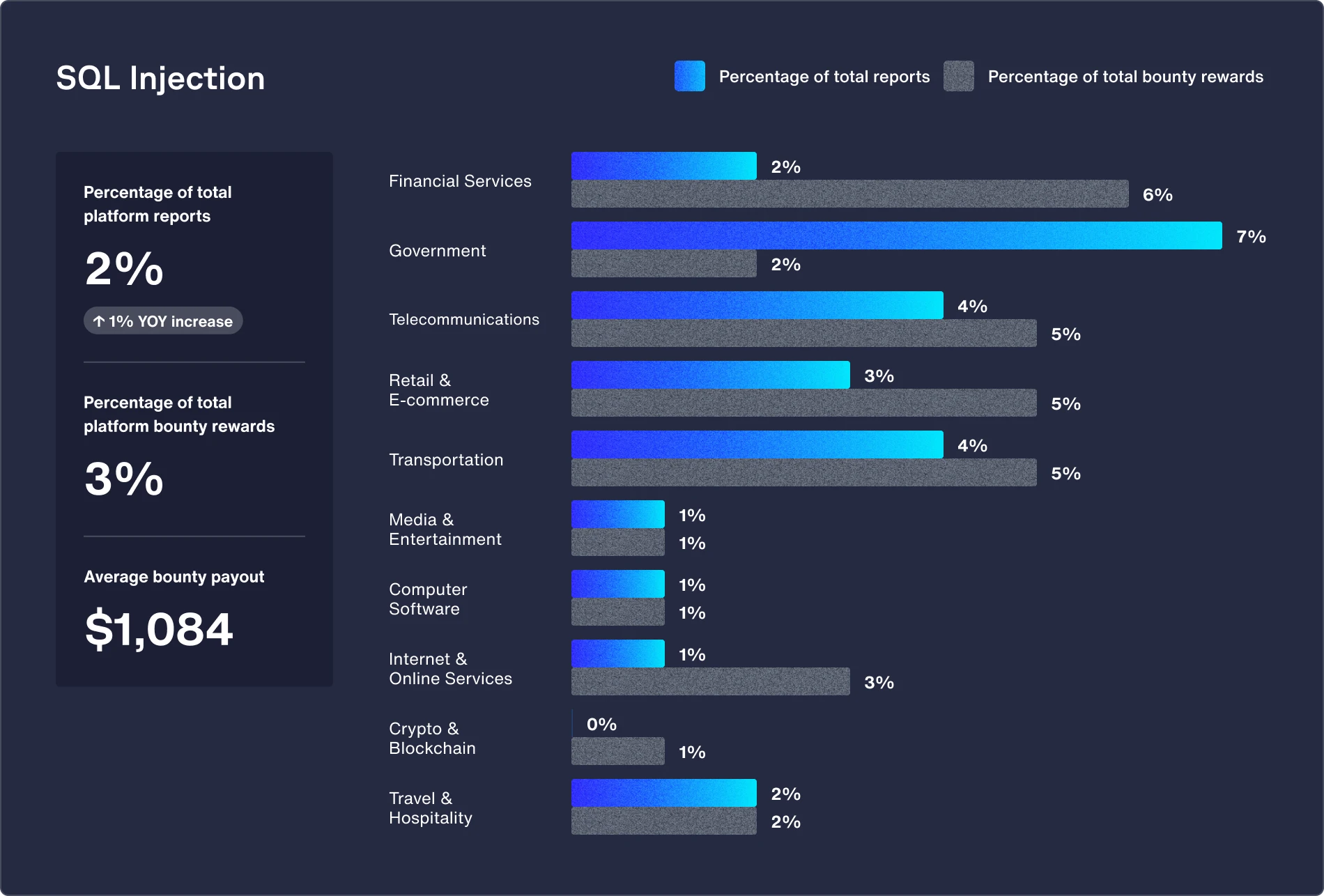
Featured vulnerability: SQL injection (up 93% from 2023)
The industry still relies on legacy systems developed before modern security practices became widespread. These older systems often lack proper input validation and secure coding, making them vulnerable to SQL injection, especially with the growing demand for web and mobile interfaces.
Recommendations:
- Implement prepared statements (parameterized queries) to separate SQL code from data, ensuring that user input cannot alter the query structure and intent.
- Validate and sanitize all user input to identify and remove potentially malicious data before processing any SQL query.
- Employ web application firewalls (WAFs) to detect and block SQL injection attempts, conduct regular security audits and penetration tests, and educate developers on secure coding practices.
Media & Entertainment
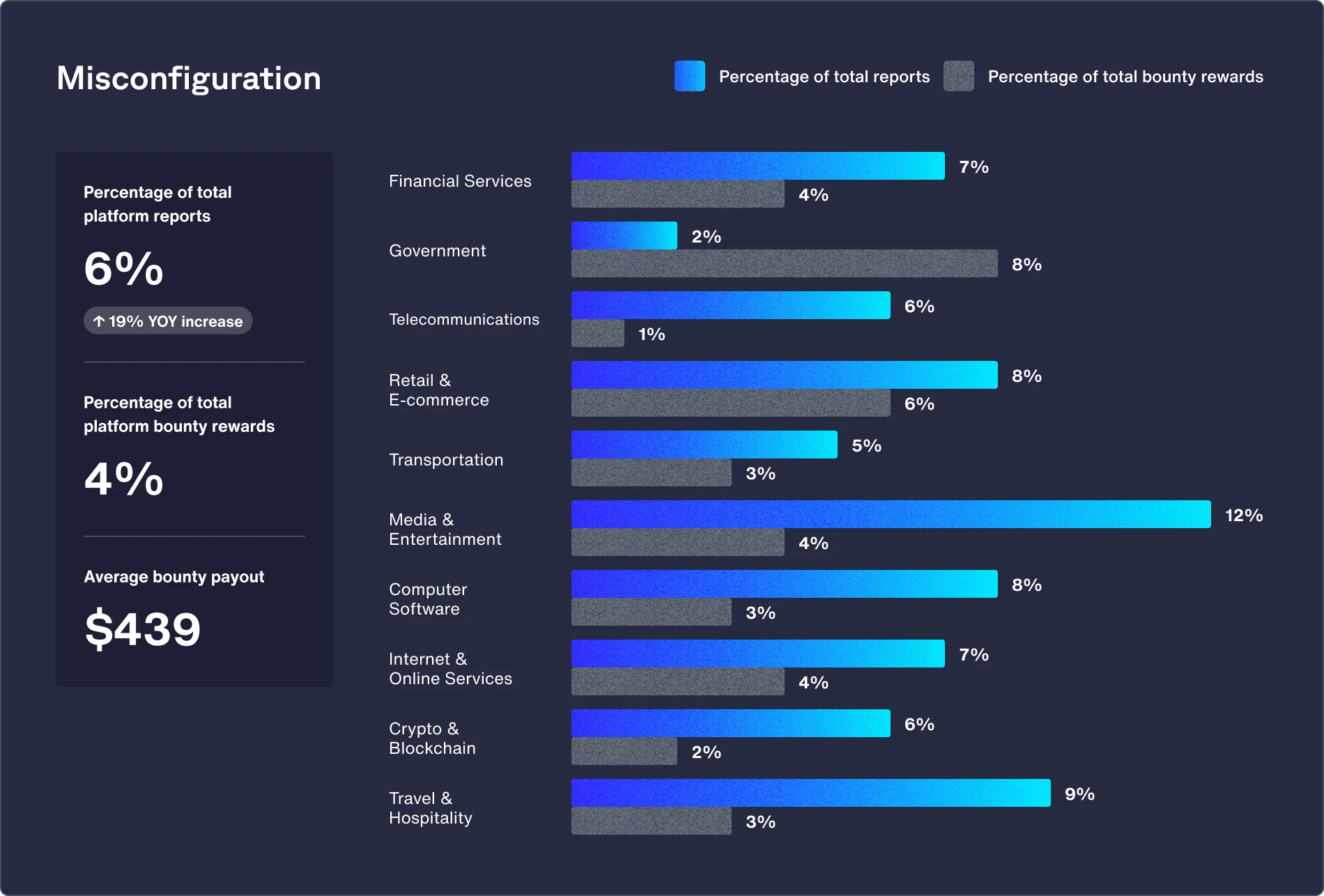
Featured vulnerability: Misconfiguration (up 69% from 2023)
This sector typically relies on complex content delivery networks (CDNs) and streaming platforms to distribute their content globally, which can lead to misconfigurations, especially when it comes to security settings and access controls.
Recommendations:
- Implement the use of automated configuration management tools and create standardized patterns to maintain consistent and secure settings across the system.
- Regularly perform security audits and reviews of system configurations and network architecture to identify and remediate any misconfigurations, unnecessary services, and open ports that could lead to security breaches.
- Implement a “least privilege” policy to restrict users, accounts, and computing processes’ access to only the resources necessary for their legitimate functions.
Computer Software
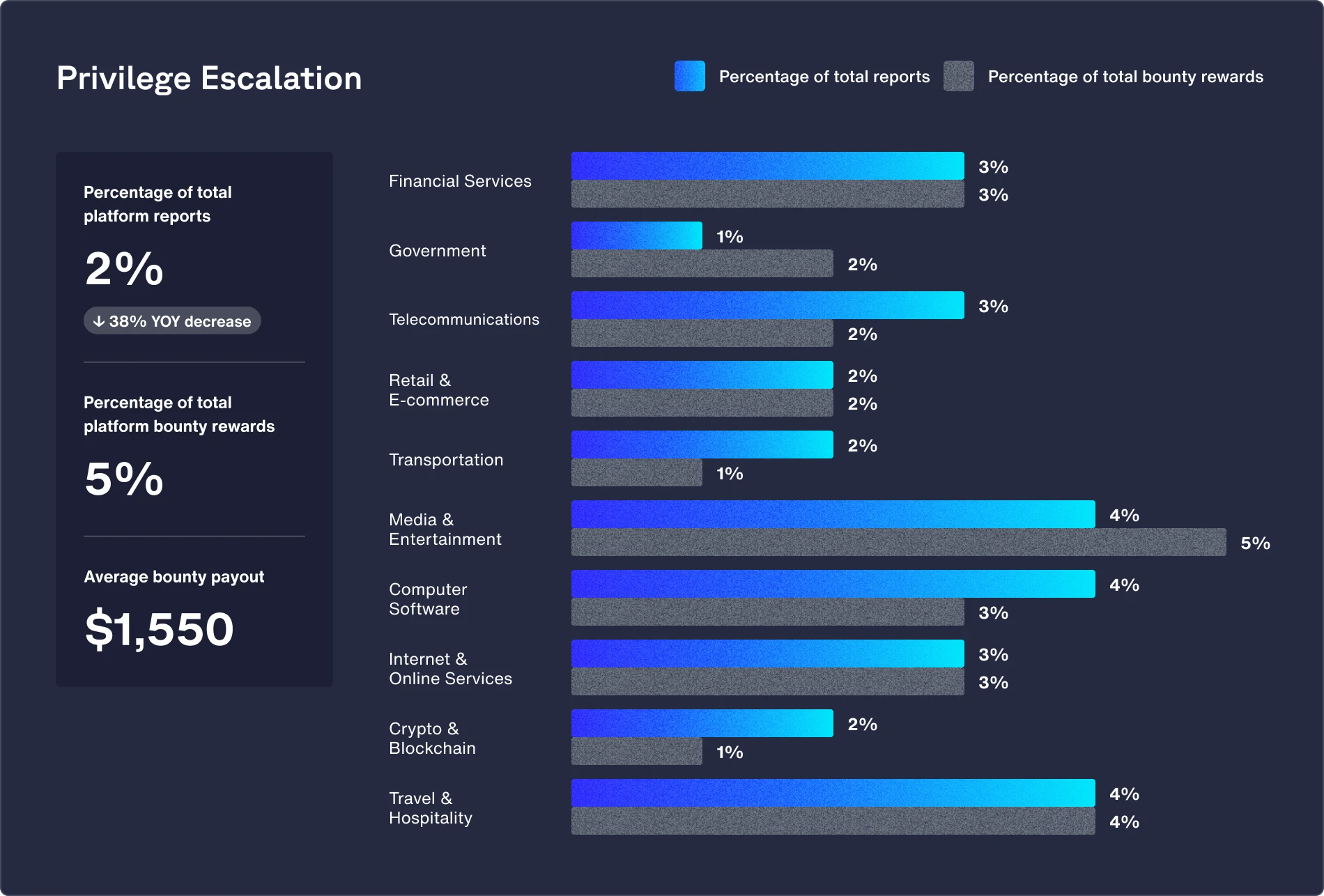
Featured vulnerability: Privilege escalation (down 2% from 2023)
Software products often serve a range of user roles, from regular users to administrators, each needing different access levels. Inconsistent permission checks, especially in enterprise software, can open the door for attackers to escalate privileges.
Recommendations:
- Implement the “least privilege” policy and role-based access control (RBAC) to restrict user permissions, ensuring access is limited to necessary resources based on specific roles.
- Implement security tools such as privileged access management (PAM) for granting access, and intrusion detection/intrusion prevention systems (IDS/IPS) for monitoring and alerting of any privilege misuse or anomalies.
- Keep your applications and systems up to date and perform regular security audits and prompt patching of software and dependencies to help address potential vulnerabilities.
Internet & Online Services
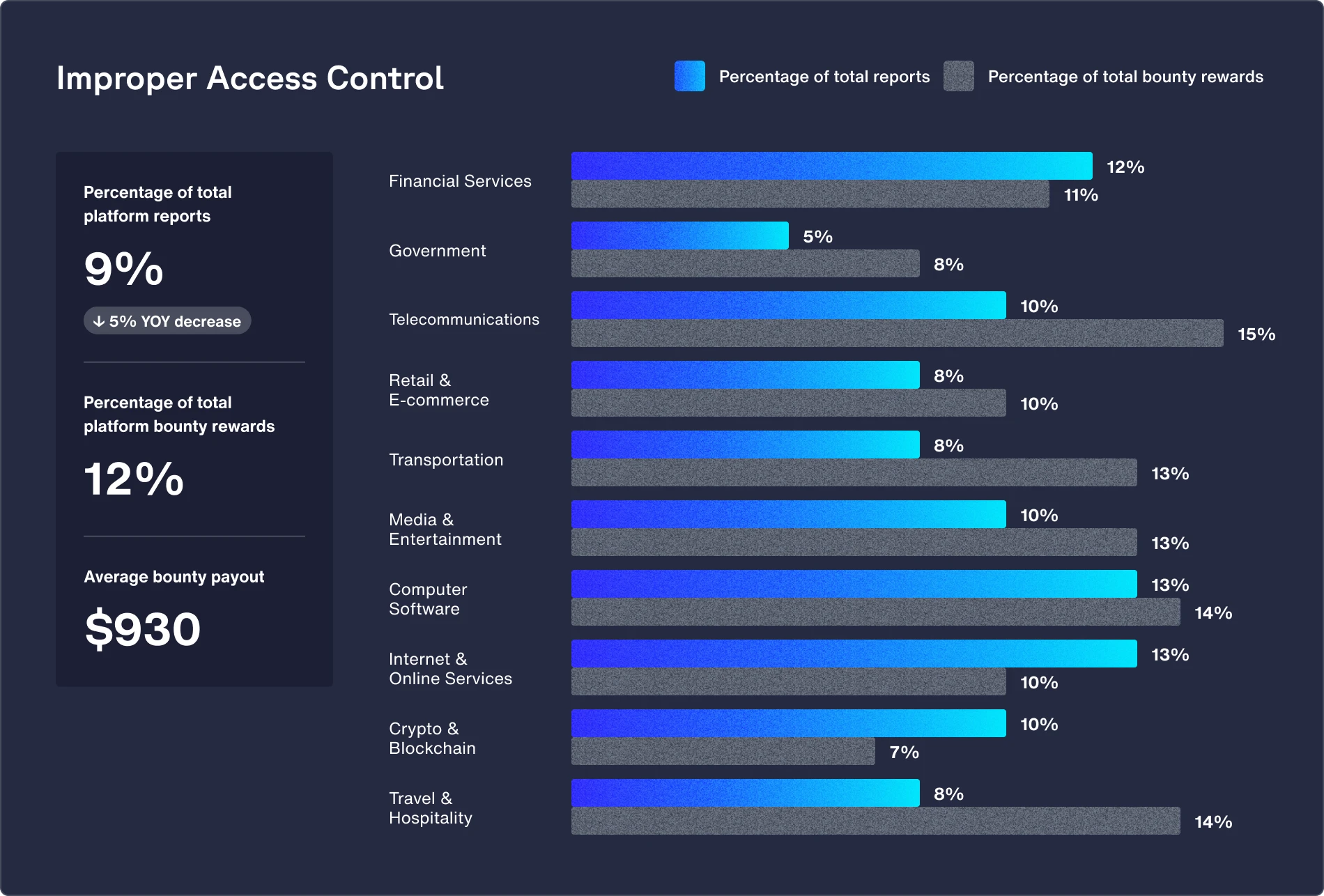
Featured vulnerability: Improper access control (up 28% from 2023)
The push to scale quickly and roll out new features makes it tough to enforce strict access controls consistently. Agile development practices, with continuous integration and deployment, often prioritize speed and innovation over rigorous security checks, which can lead to access control vulnerabilities slipping through.
Recommendations:
- Define and enforce user roles and permissions using role-based access control (RBAC). Use the “least privilege” principle to grant users and systems the minimum level of access they require to perform their functions.
- Use multi-factor authentication (MFA) for secure access. Re-authenticate users when executing sensitive functions.
- Ensure proper session management is implemented by using secure cookies, expiring sessions appropriately, and avoiding persistent tokens unless necessary.
Crypto & Blockchain
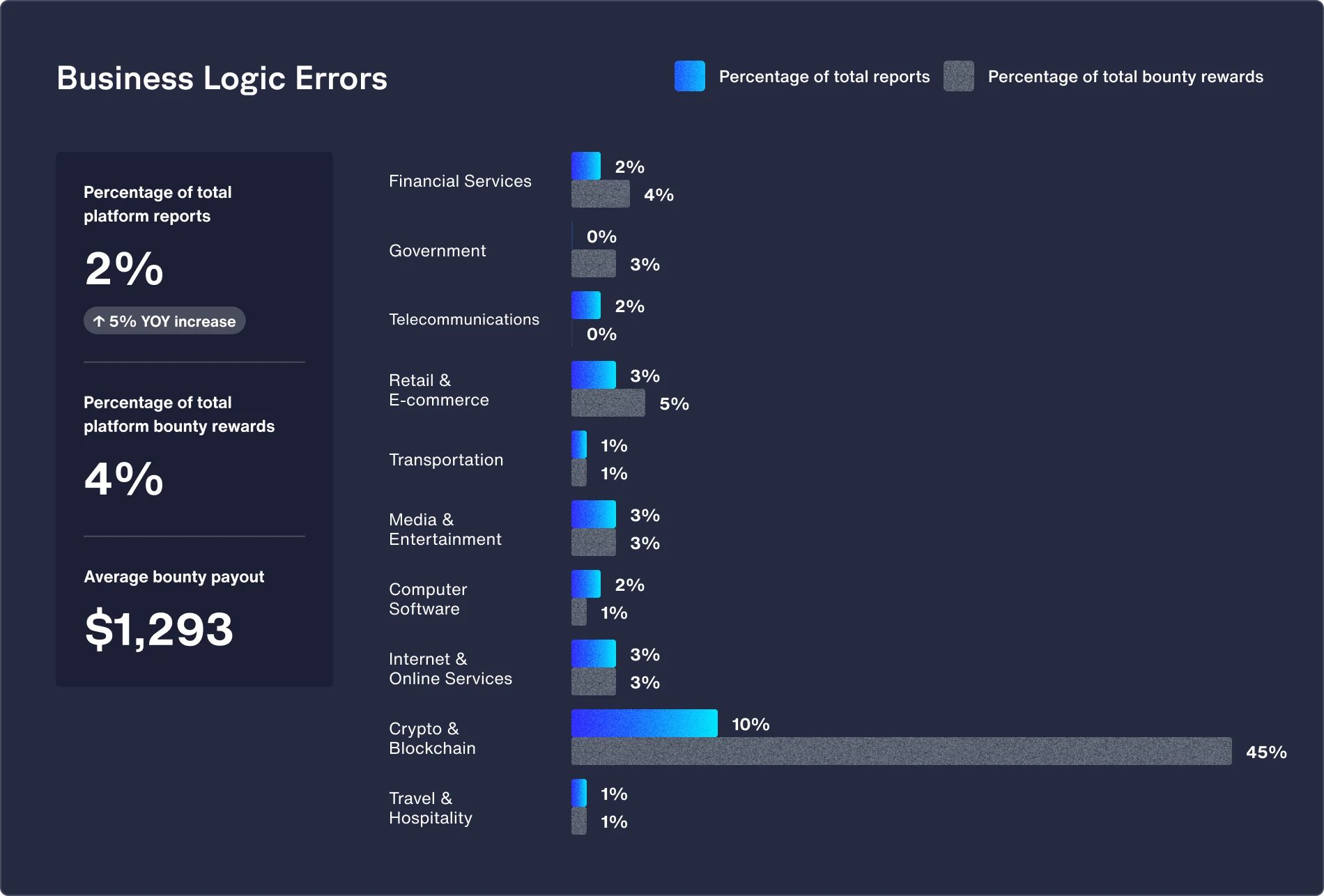
Featured vulnerability: Business logic errors (up 37% from 2023)
With their complex, experimental business models and intricate transaction mechanisms, it’s tough for crypto and blockchain organizations to secure against edge cases or unintended uses, meaning any flaws or logic errors are hard to fix.
Recommendations:
- Use test-driven development (TDD) and extensive unit and integration testing to simulate various scenarios and edge cases.
- Enforce multi-signature requirements for critical operations to reduce the risk of flawed transactions.
- Design smart contracts with role-based modules to isolate critical operations, ensuring that only authorized users or entities can execute high-risk functions.
Travel & Hospitality
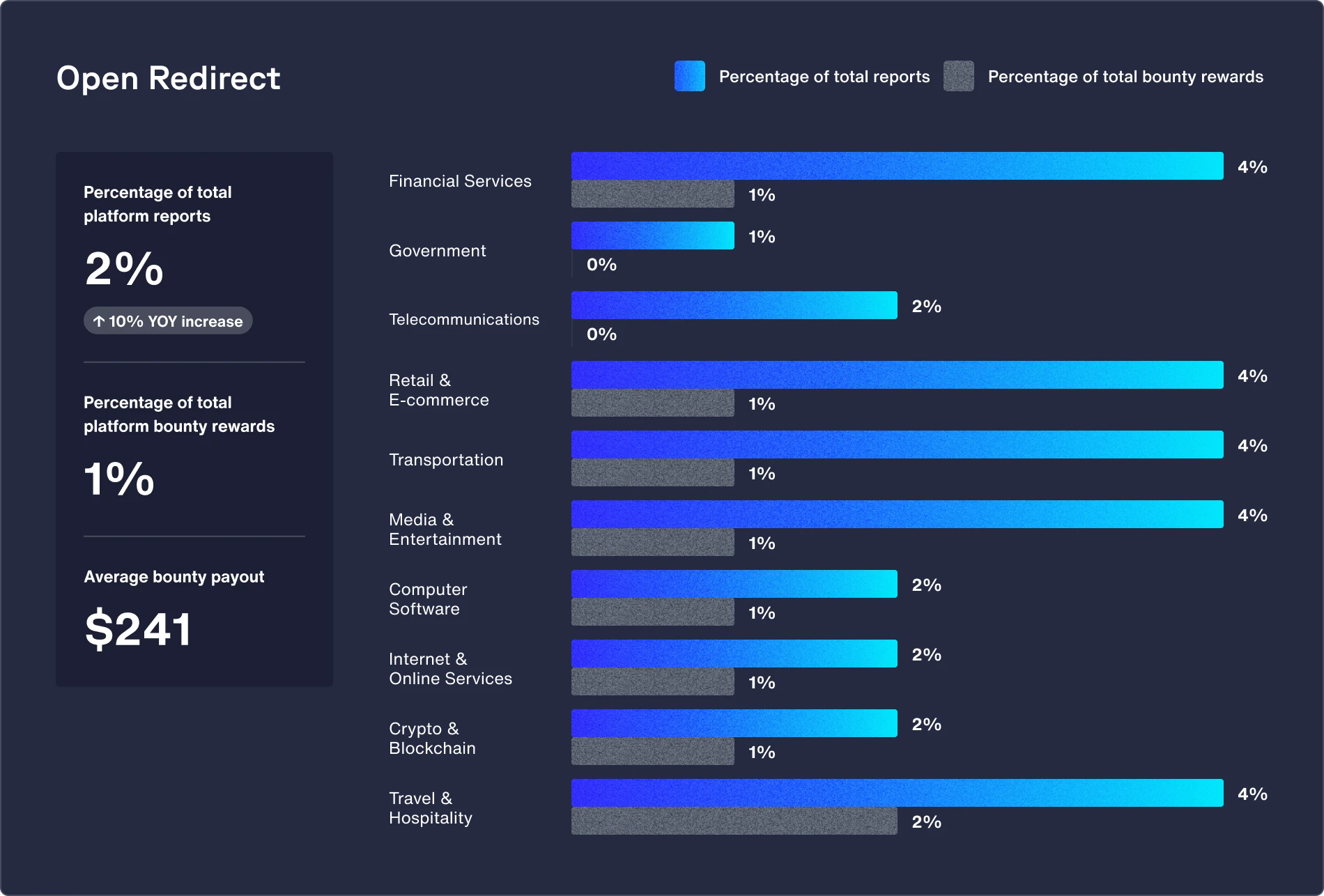
Featured vulnerability: Open redirect (up 92% from 2023)
Travel and hospitality organizations rely heavily on marketing, often embedding referral and affiliate links. Attackers may exploit open redirect vulnerabilities by tampering with these links to lead users to malicious sites.
Recommendations:
- Implement input validation and sanitization for all user inputs and avoid using user-controllable data in URLs.
- Provide clear warning for all redirects, notify users they are leaving the site, display the destination, and require a confirmation click.
- Sanitize input by creating a list of trusted URLs (lists of hosts or a regex). Implement the use of an allow list, rather than a deny list.
63% of Your Bounty Budget Will Be Spent on the Top 10
The vulnerabilities organizations allocate their budgets to don’t always align with the volume of reports for those vulnerabilities.
Recommendations
Identify the critical systems, applications, and data that will be in scope for the program, prioritizing high-value assets.
As your program evolves, monitor report volume, payout levels, and researcher feedback to adjust budgets over time.
Prepare for unexpected high-severity vulnerabilities by having a buffer in the budget for critical vulnerabilities that may require higher-than-anticipated payouts, ensuring that you can address major security threats without financial constraints.