of researchers hack full time
03
Automation Can’t Compete: Security Researchers Prove Their Edge
spend over 20 hours a week hacking
Researchers are motivated by:
Researchers test on:
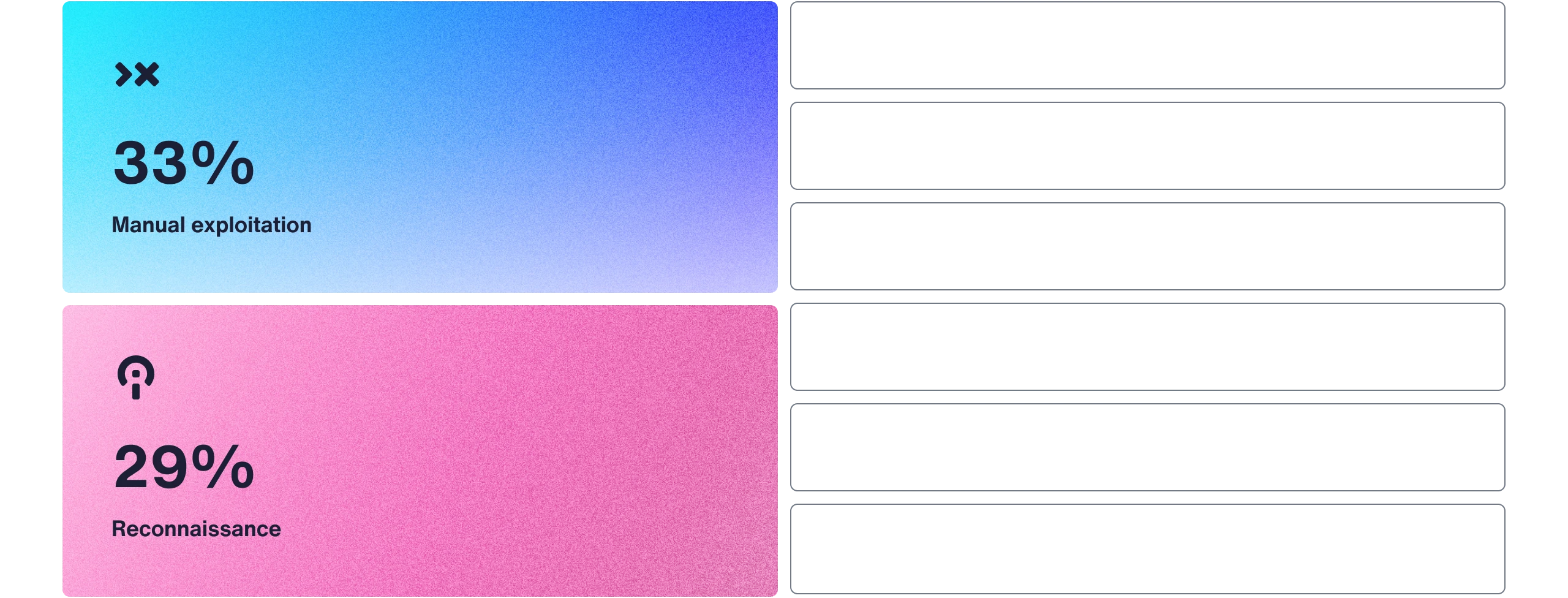
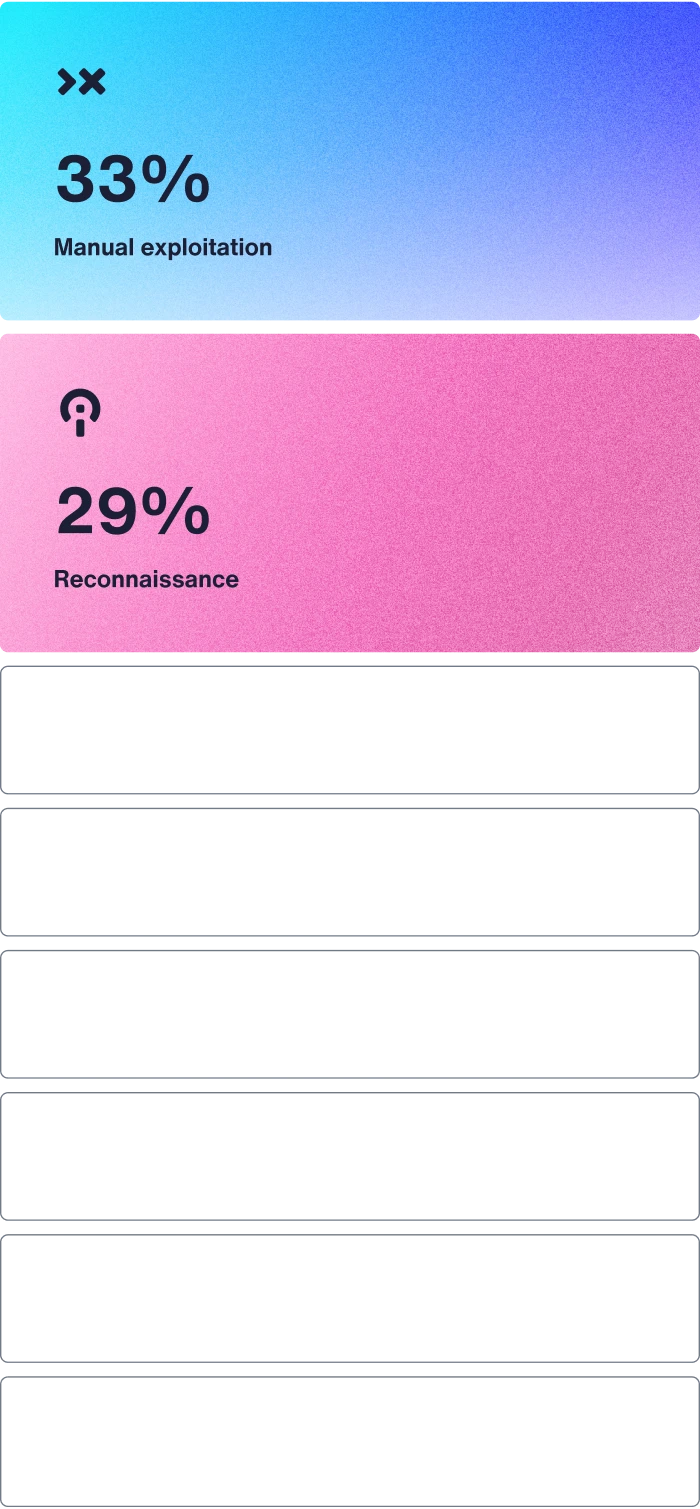
Security researchers excel in reconnaissance and manual exploitation—two key hacking skills that automated scanners can't match.
The more you and your organization know and understand about researchers and their motivation, and approaches, the stronger the relationship will be and the more impactful your program will be.
Researchers think they are most skilled at:
Recommendations
Clearly communicate expected response times for report acknowledgment, triage, and resolution. This builds trust and helps researchers understand when they can expect feedback.
Offer constructive feedback on the report, explaining the vulnerability’s impact and any necessary remediation steps.
Respond to researchers with respect and professionalism, even if the report is invalid or a duplicate. Positive interactions encourage ongoing collaboration.
Download the Full 8th Annual Hacker-Powered Security Report
Get researcher insights, customer testimonials, industry data, analysis and advice, and more.